The Pandemicsituation shift work culture from working in the office to work from office created major challenges for business worldwide. FormingDigital infrastructure to Business which is relying on digital services to maintain supply chain for essentials, while minimizing social contact.
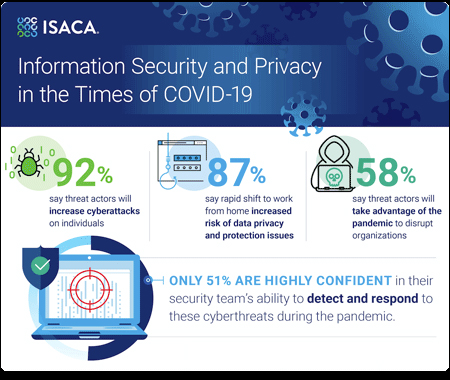
The demand placed for Digital Infrastructure, DigitalServices and Digital channels are rising to maintain business continuity in COVID 19 Pandemic.Cyber incidents are consistently ranked at the top of business concerns, According to one estimate,the global cost of cybercrime will rise to $6 trillion a yearby the end of 2021.Since the pandemic began,Marriott suffered a data breachaffecting 5.2 million customers, and aransomware attack forced Honda to shut down global operations.According to the Federal Trade Commission, by mid-August 2020 there hadbeen more than 172,000 fraud reports related to the pandemic itself, at the cost of about$114.4million.
vulnerability during the pandemic
Cybercriminals expected employees to have access to corporate VPNs, cloud-based services, and business email, all of which could be used for infiltration of corporate assets if not properly secured.
In addition, we’ve seen many campaigns using the fear of COVID-19 as the theme for their malicious activities.
- Information-stealing scams. Hackers embed code into websites that look real and provide legitimate information about the coronavirus. For example, hackers created an identical version of a map of global COVID-19 cases with embedded malware.
- Ransomware and malware attacks. Netwalker, a strain of ransomware, is using files with coronavirus in the name so that they look important. The files embed code that will encrypt your files.
- Work-from-home vulnerabilities.These include unprotected videoconference links or hacked videoconference passwords, which can be used to access a company’s network. Also, some people working from home might be using unsecured networks.
- Fake products. Several websites purport to sell masks or coronavirus remedies, but take money from customers without providing any product. Others sell fake face mask exemption cards purporting to come from a government agency.
Cyber Hygine Practices of Company and Employess
Employees working from home and using their personal computer (and even those using a corporate-owned device) should implement essential cyber hygiene practices. These include:

- Antivirus protection. Employees should be provided with a license to antivirus and malware software for use on their personal computers. Although this does not provide failsafe protection, it eliminates many low-level attacks.
- Cyber security awareness. Staff should be briefed on best practices and procedures to regulate the sending of emails or other content to private email addresses and/or cloud storage.
- Phishing awareness. Employees should be vigilant when receiving emails and should check the authenticity of the sender’s address.
- Home network security. Employees should ensure that their home Wi-Fi is protected by a strong password.
- Use a VPN. Virtual private networks add a further layer of protection to internet use from home. They cannot on their own be relied upon to prevent cyber attacks, but they can be a useful barrier against cyber attack. There are some basic cyber security strategies that businesses can adopt.
- Identify weak spots. All IT systems have weaknesses. Companies should run tests to identify them and patch the most critical vulnerabilities as soon as possible. This can take the form of vulnerability scanning, or various type of penetration testing exercises. Additionally hardening of components of the technical infrastructure should be performed.
- Frequent reviews. Companies should regularly evaluate cyber security risk exposure and determine whether existing controls are robust enough. Any new forms of cyber attack that have appeared recently should be considered during these reviews.
- Renew business continuity and crisis plans. Business lines Managers need to keep their business continuity plans updated and consider cyber attack scenarios.
More advanced measures that can be taken include:
- Apply new technology and tools. Companies can use advanced tools such as host checking (a tool to check the security posture of an endpoint before authorizing access to corporate information systems) to reinforce the security of remote working.
- Intelligence techniques. Businesses should encourage proactive use of cyber threat intelligence to identify relevant indicators of attacks (IOC) and address known attacks.
- Risk management. Businesses can apply governance, risk and compliance (GRC) solutions for improved risk management. GRC solutions provide a
detailed view of the company’s risk exposure and help link together the various risk disciplines (e.g. cyber security, operational risks, business continuity).
- Prepare for attacks. In these high-risk times, companies are advised to carry out frequent cyber crisis simulation exercises to prepare their response to a cyber attack.
- Zero Trust. CISOs and CIOs should consider implementing a zero trust approach to cyber security. This is a security model where only authenticated and authorized users and devices are permitted access to applications and data. It challenges the concept of “access granted by default”.
After Covid-19
It’s important to remember that Covid-19 is expected to be temporary, after completion of this pandemic it is difficult to reversed once and new habits will persist,need to worry about IT security pros need to implement new security. Here need to discuss speculation about after Pandemic scenario.

- Some organizations will need to move to new operating models. For these companies, immediately after the crisis, cybersecurity and IT rights will require careful examination and handling. Remote worker monitoring and support will become vital. And for workers who transition from home back to the office, cybersecurity professionals must ensure stringent system and access scrutiny prior to allowing the shifted system to connect back to the network.
- Companies will need to reset their security systems to ensure there are no outliers. Both physical and digital systems will need to be restarted, to check for any digital holes in the fence. System and data access rights granted during the pandemic to enable remote work will require auditing to determine whether they should be revoked or updated. IT systems will need to be analyzed for cracks, foul paths or fraudulent identities. The reason is that cybercriminals may have found ways to gain entry into otherwise hardened facilities.
- New cyber risks that appeared during the pandemic must be understood. For instance, security experts will need to scrutinize the digital capabilities of critical business functions, making sure they can withstand cyberattacks during a lockdown. They will examine critical supply chains, including digital supply chains, to ensure continuity during a health crisis.
- Corporate IT security architectures should be reassessed. This includes access mechanisms, support needs for remote access on a mass scale, and feature risk/context-based security authentication mechanisms.
- Updates to remote access and bring-your-own-device (BYOD) policies must be made. They should include cybersecurity hygiene controls.
- Advanced technology must be deployed. Threat detection and response capabilities must include advanced capabilities supported by next-generation technologies like big data, artificial intelligence and machine learning. These are needed to detect and respond to adverse behaviour at machine speed, without human interventions. Further, organizations will want to explore insurance against losses from cyber attacks incurred during a pandemic scenario.
Conclusion
companies should be proactive in addressing the threats, and plan ways of preventing successful cyber attacks rather than responding when they occur. However although prevention measures are important, there is also a need for cyber attack detection, response and recovery capabilities. This pandemic has taught us that preparation is key to successfully limiting the risks related to cyber attacks. The ability to quickly react to unforeseen events helps reduce the impact of a cyberattack. Companies that already benefited from secure remote working capabilities will be better prepared to face the continuous increase of cyber threats. Regular staff training should include the full range of issues related to cyber security, including malware, phishing, username and password management, data protection, encryption, home network security, network connectivity (VPN) and endpoint security – and employees’ knowledge needs to be kept up to date.
Employees also need to familiarise themselves regularly with rules and guidance on handling confidential data, including the penalties they may face for making improper use of data.