Introduction
Cybersecurity is an inclusive concept; it not only has wide ramifications cutting across Societies, Government and Businesses, it also directly impacts human behavior - whether co-operative or malefic. The span, reach and impact of Cyber/Infosecurity is incumbent on a slew of factors, viz; pace of digital transformation, changing threat landscape and macro-level policies and frameworks. Cybersecurity can take many forms but the most commonly discussed topics are around applications, data/info, cloud, and data-centers.
The threat landscape has changed significantly over the past two years since the start of the pandemic, and while businesses are trying to cope up with the evolving scenarios, there is much room for improvement. The rapid pace of digital transformation, while ensuring continuity of businesses, has also exposed large gaps in Cyber-readiness, preparation and threat identification. Part of this can be attributed to the evolving Hybrid work models across sectors and the constant threat of non-state actors.
While cutting-edge technologies such as AI/ML and Cloud riding the adoption wave have given a fillip to security response posture across business landscape, it is believed to be just one of the cogs in the wheel.
“Cybersecurity is a Covid-19 resilient horizontal vertical along with Workplace Modernization and Cloud Transformation.”
Cybersecurity Product Landscape in India
As per a DSCI & PwC report, the key developments within the Indian Cybersecurity technology space can be summed up as follows:
- Earned revenues of US$1,016mn in 2020
- Grew at a compounded AGR of 39% between 2016 and 2020.
- Has an installed Cybersecurity talent of 18,000 (as of 2020)
- A total of 225+ companies (up from 185+ companies in 2018) and start-ups within the ecosystem.
- The product industry grew 2X in just 2 years - between 2019 and 2021
- The strong growth within the ecosystem is expected to sustain over a period of time
- Cumulative PE/VC funding of US$490mn in the sector (2017-2020)
India has ambitious targets in this space; to emerge as the next-gen Cybersecurity hub, powered by both the Product as well as the Services stack. Incubation and acceleration programs designed to capture mindshare, the co-ordination among the Industry (Systems Integrators, Managed Service Providers & Start-ups), Academia, and the government are all geared up to promote innovation and products for new and complex use-cases. World over, and not just in India, Phishing, Malware and Social Engineering have emerged as the top Cyber-threat categories. In India alone, targeted Cyber attacks towards businesses have grown 3 times in 2020 over 2019 (11,58,206, up from 3,94,000 in 2019). `
What is needed is Next-gen Cyber products & services, framework & policies and more importantly evangelization for Cyber adoption. There is a need to sensitize, drive awareness and Cyber-readiness to the next level leveraging innovation and product development.
“DSCI’s vision to make India a Global hub for Cybersecurity and a US$35B bn industry by 2025, is led by the twin engines of Services and Products”
Key trends shaping up the landscape
"One of the key challenges for decision-makers is to handle the dichotomy of optimization of resources and increasing Cyber capabilities."
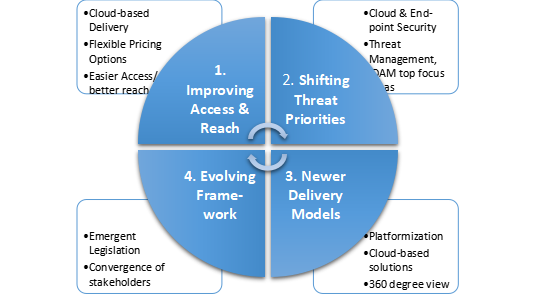
With the integration of enabling technologies with new-age security solutions, it is becoming easier for businesses to start on their journeys, particularly within the SMB and Public sectors including Government, Healthcare and Education. New market sentiments and changing threat scenarios is forcing a shift in priorities and re-calibration of governance models, frameworks and applicable laws. The shift can be attributed to the following factors:
- Improving Access and Reach:
- Easier access to new technologies, ensuring reach
- Sophisticated as-a-service models (licensing/subscription-based) evolving
- Shifting Threat Priorities
- Cloud & end-point security gaining traction due to large-scale Digitalization efforts and proliferation of devices
- Higher cost of security breaches owing to hybrid work models
- Threat Management, Identity & Access and securing distributed workforce identified as top challenges
- Newer Delivery Models:
- Platformization and maturing cloud-based delivery models
- RPA/Automation and AI/ML tools bringing in cost optimization in functions like threat identification, assessment
- Consolidating architecture, tools, methodologies and licenses to achieve a 360° view of the security apparatus
- Evolving Legal/Policy Frameworks
- Emergent legislation to safeguard CNI (Critical National Infra.)
- Bringing together institutional structures, people, processes and technologies
Cyber Advocacy - What is it?
In view of the developments cited above, there is a need for advocating the need for and use of Security as a key business input, particularly from the standpoint of protecting digital identities, safeguarding customer data and keeping applications safe to ensure business continuity. Despite best efforts, higher budgetary support and an understanding of the threats, it is difficult to achieve the minimum credible deterrence at the business level most of the times. There clearly, is a need to promote Cyber/Info/Data security across societies, government and businesses.
Cyber/Security Advocacy is an emergent discussion topic both at the level of the CIO/CISO as well as on the side of the business. The contours of the key responsibility areas (KRAs) are still being debated, modified and refined. However, there is some convergence in terms of what Cyber Advocacy involves, though still evolving:
- Identifying a single, unified view of risks across the entire Cybersecurity landscape
- Builds, promotes and maintains Cyber awareness and a culture of adoption across the organization
- Measures Security awareness and communications program
- Achieving jointness among a diverse group of stakeholders
- Establish a robust security posture and industrialize its adoption at every level.
- Promoting Data Security
- Promoting global best practices
- Imbibing relevant skills - Technology & Interpersonal
- Establishing context awareness
- Influencing and securing user/workforce behavior using technologies like Analytics
- Achieve buy-in of decision-makers with respect to technologies, investments and policy
A key component of Cyber Advocacy is legal advice. NICCS (National Initiative for Cybersecurity Careers and Studies) defines this as Cyber Legal Advisor who provides legally sound advice and recommendations to the leadership on a variety of relevant topics within the domain.
Some of the other similar roles extant globally are:
- Privacy Compliance Manager
- Security Awareness and Communication Manager (NIST framework)
- Security Awareness Professionals
- Secure Development Champions
- Security Consultant
- Security Advocacy Staff
Or, in other words, Cybersecurity Advocates are security professionals who are entrusted to promote and encourage security adoption as a major component of their job. They help complement basic security practices and technologies. Another aspect is to be able to clearly articulate the changing threat landscape through effective communication of security risks, enabling change in behavior.
Need for Cyber Advocacy in India
Cyber Advocacy is a nascent concept in India and it is short of receiving the attention it deserves. Currently, practitioners from the Legal community form the bulk of this space. In the coming years, Cyber Advocacy as a concept needs to evolve beyond the confines of the legal framework and encompass a holistic approach. From an enterprise perspective, the following are the some of the triggers that can bring the concept of Cyber Advocacy to the forefront:
- Being a champion for practitioners/profession: One of the key success factors for the study and practice of Cybersecurity is the need to define the roles that the workforce is expected to carry out. In fact, clearly defined roles, skills and work areas can not only help to assess the contours of the Cybersecurity practice, but can also help to plan forward for manpower requirements and associated skills.
- Change Agents for Cybersecurity Adoption: As per an assessment made by Cybersecurity Ventures, the Global cost of cyber attacks could surpass US$6 trillion in 2021. As mentioned earlier in the article, the number of Cyber attacks in India has also risen 3-fold. While best practices are followed, attacks do take place costing businesses money, reputation and trust. Cyber Advocates can help reduce the risk further through promotion, education, and adoption of Cybersecurity.
- Developing Context Awareness: Technologies work in tandem and not in isolation. Digital technologies have multiple overlaps involving different domains which is both a boon as well as a challenge. In Cybersecurity there are multiple aspects - data, cloud, network, end-point and others. On the enabler side, there are key Digital technologies such as AI/ML, Cloud-based platforms, automation etc. A Cyber Advocate can play a big role in establishing a 360° view of the operations, processes, people and technologies. They can bring together disparate aspects of the entire Cybersecurity landscape to set the context, expectations, awareness among the stakeholders including CXOs, users, suppliers, and even the competitive landscape.
In the forthcoming articles, we shall try to delve deeper in to Cyber Advocacy from a role perspective, to try and bring out the nuances of the role, evolving skills expectation and the core work areas.