In today’s digital landscape, where nearly every interaction leaves an online trace, safeguarding our digital environments is more crucial than ever. As we navigate personal and professional realms, technology offers innovation while presenting cybersecurity challenges.
As data grows and cloud computing becomes increasingly widespread, maintaining security is crucial. The cloud, where we store sensitive information, requires protection and a steadfast defence against evolving cyber threats.
In this digital landscape, traditional security methods face challenges. Passwords and PINs, once reliable, now struggle against sophisticated cyber threats. Biometric authentication emerges as a leading-edge solution gaining traction in software and cloud computing, delivering unparalleled improvements in both security and user experience.
Biometrics, blending advanced technology with our unique physical and behavioural traits, is not just a security upgrade; it's a shift in how we safeguard digital assets. In the world of ones and zeros, biometric authentication weaves precision and convenience into the very fabric of security.
As we explore further, the journey takes us through a technological revolution. Fingerprints, faces, voices, and behaviors are now serving as digital keys, making our online defenses significantly stronger.
What is Biometric Authentication in Software and the Cloud?
Imagine accessing your favorite software applications or sensitive cloud-based data with just a touch of your finger or a glance at your face – that's the power of biometric authentication in the cloud and software.
Biometric authentication confirms who you are by using your unique physical traits. These characteristics, known as biometrics, include your fingerprint, iris pattern, or even your face, to confirm your identity. In software and cloud computing, this technology swaps out old login methods with something more secure and user-friendly.
Here, we go into the transformative nature of biometric authentication, highlighting its precision, convenience, and its role in enhancing security creating the digital trust landscape.
Types of Biometric Technologies
|
|
Biometric Technology
|
Type
|
Features
|
Characteristics
|
Applications
|
Real-Life Applications
|
Physiological
|
Fingerprint
|
Unique patterns in ridges and valleys
|
High accuracy, widely adopted
|
Access control, device authentication
|
- Unlocking smartphones and devices with fingerprint sensors.
- Physical access to buildings, secure areas, and data centers.
|
|
Hand Geometry
|
Analyzes the size and shape of the hand
|
Non-intrusive, suitable for physical access
|
Workplace access, time and attendance
|
- Controlling access to offices and sensitive areas.
- Tracking employee attendance with hand scanners.
|
|
Iris Scanning
|
Examines patterns in the iris of the eye
|
High-precision, non-contact
|
Airport security, national ID systems
|
- Identity verification in airport security checks.
- Enhancing security in national identification systems.
|
|
Facial Recognition
|
Identifies based on facial features and proportions
|
Non-intrusive, fast identification
|
Surveillance, mobile security
|
- Identifying individuals in CCTV footage for security purposes.
- Unlocking smartphones and authorizing mobile payments.
|
|
DNA Biometrics
|
Analyzes unique genetic code
|
Highly accurate, definitive identification
|
Forensic investigations, medical research
|
- Solving crimes and identifying individuals from biological samples.
- Studying genetic information for medical and research purposes.
|
|
Behavioral
|
Keystroke Dynamics
|
Studies unique typing patterns and rhythm
|
Continuous authentication, non-intrusive
|
User authentication, fraud detection
|
- Verifying users based on their typing patterns.
- Detecting anomalies in typing behavior for fraud prevention.
|
|
Signature Recognition
|
Analyzes the unique way an individual signs their name
|
Individualistic, common in legal processes
|
Financial transactions, document verification
|
- Verifying signatures on checks and legal documents.
- Authenticating documents and contracts.
|
|
Voice Recognition
|
Captures and analyzes unique vocal characteristics
|
Non-intrusive, natural user interface
|
Voice-controlled systems, call center authentication
|
- Enabling voice-activated commands on smart devices.
- Authenticating users during phone interactions.
|
How Does Biometric Authentication Work?
How does your device know it's you? It all starts with enrollment. When you first set up biometric authentication, your device captures a snapshot of your biometric data and converts it into a digital template. This template is then stored securely on your device or in a central database or the cloud.
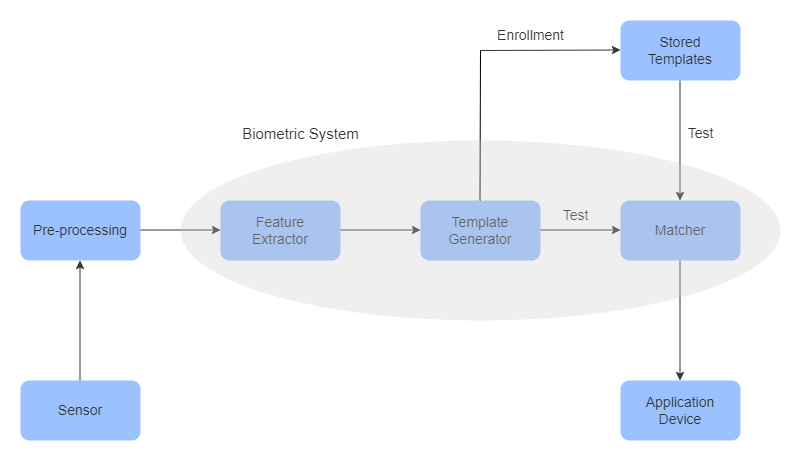
When you try to unlock your device or access a secure system, the biometric sensor scans your chosen biometric feature – whether it's your fingerprint, iris, or face. This scan is then compared to the saved template. If there’s a match, you're granted access almost instantly. This seamless process eliminates the need for remembering complex passwords or carrying around physical tokens.
Advantages of Biometric Authentication in Software and the Cloud Over Traditional Methods
So, why bother with biometrics when good old passwords seem to do the trick? Here are a few reasons why biometric authentication is the way forward:
Enhanced Security
Unlike passwords, which are easy to forget, guess, or steal, your biometric data is truly one-of-a-kind. This makes it incredibly tough for the wrong people to get into your accounts. Because biometric traits are unique to each person and hard to copy, unauthorized access drops significantly.
Convenience
Gone are the days of struggling to recall passwords or dealing with cumbersome authentication processes for security token. With biometrics, you can get into accounts easily with just a touch or a glance.
Speed
With biometric authentication, accessing software applications or cloud services is lightning-fast. A quick scan of your fingerprint or facial recognition is all it takes to gain entry, saving valuable time.
Reduced Risk of Credential Theft
Biometric authentication helps combat fraud by making it nearly impossible for impostors to impersonate the individual. Whether it's preventing unauthorized access to your smartphone or securing sensitive financial transactions, biometrics add an extra layer of protection against fraudsters. This lowers the chance of someone stealing your login details or getting into sensitive information stored in the cloud or software apps.
Eyes: The Gatekeepers of Biometric Security
A. Iris Recognition Technology
How Iris Recognition Works
Iris recognition is a sophisticated biometric technology that relies on capturing and analyzing the unique patterns present in the colored part of our eyes, known as the iris.
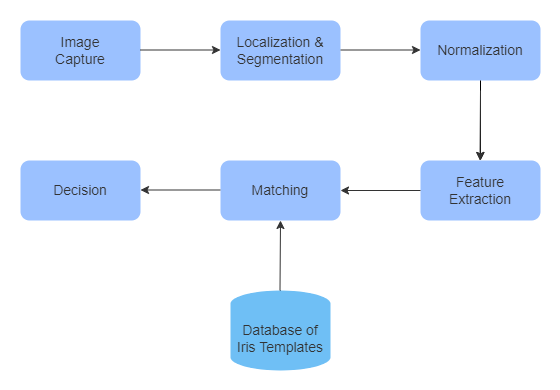
Image Capture
Specialized cameras with near-infrared (NIR) light can capture clear pictures of your iris, which is the colored part of your eye around the pupil.
-
The NIR light is used to illuminate the iris, making it easier to capture details such as crypts, furrows, and collarette patterns.
Localization & Segmentation
Software algorithms analyze the captured iris image to locate and isolate the iris region within the image.
Normalization
Once the iris region is identified, the captured image undergoes normalization to standardize its size, orientation, and position.
-
Normalization process corrects for variations in pupil size, eyelid occlusions, and imaging conditions, ensuring consistency in feature extraction.
Feature Extraction
Unique features are extracted from the normalized iris image to create a digital representation of the iris.
-
Features extracted may include patterns such as crypts, furrows, freckles, and collarette patterns.
-
These features are quantified and represented mathematically as a series of numbers or codes, forming an iris code or template.
Matching
The extracted iris features from the captured image are compared against a database of stored iris templates.
Database of Iris Templates
The system maintains a secure database containing the stored iris templates of enrolled users.
Decision
The system evaluates the similarity between the extracted features and the stored template. If the level of similarity surpasses a predefined threshold, the user's identity is confirmed, and access is granted. Similarly, access is denied if there's no match found or if the comparability score falls below the set threshold.
Advantages
High Accuracy
Iris recognition boasts unparalleled accuracy, with error rates lower than other biometric modalities, ensuring reliable authentication.
Stability
Iris patterns remain relatively stable over time, providing a reliable long-term biometric identifier.
Contactless
Iris recognition offers hygienic and non-invasive authentication, enhancing user convenience and acceptance.
Limitations
Cost
Implementation of iris recognition systems can be costly due to the need for specialized hardware such as high-resolution cameras, infrared illumination and software requirements.
Accessibility
Some users may experience difficulty with iris recognition due to eye conditions (e.g., cataracts) or disabilities affecting iris visibility, potentially limiting its universal applicability.
B. Retina Scanning Technology
How Retina Scanning Works
Retina scanning technology takes biometric authentication to a deeper level by focusing on the blood vessel patterns present in the back of the eye, known as the retina.
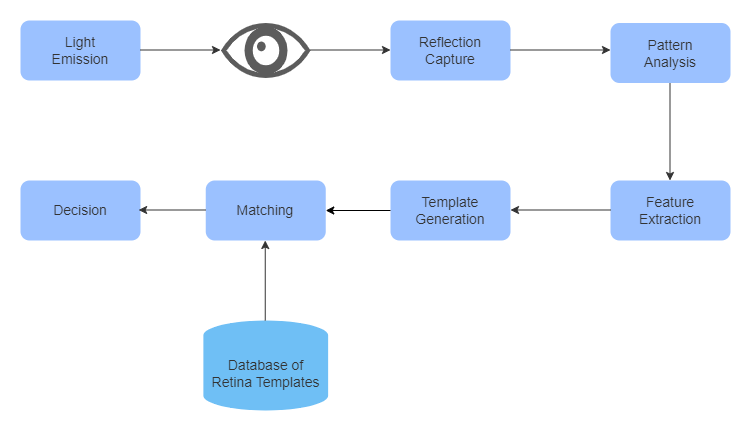
Light Emission
Specialized scanners emit low-intensity infrared light towards the eye, which penetrates and illuminates the blood vessels in the retina.
Retina
The emitted infrared light penetrates the eye and reaches the retina, which is the innermost layer of the eye containing light-sensitive cells.
Reflection Capture
As the infrared light interacts with the blood vessels in the retina, it is partially absorbed and partially reflected towards the scanner.
Pattern Analysis
Software algorithms analyze the captured image to identify and extract distinctive features and characteristics of the blood vessel patterns.
Feature Extraction
The software algorithms focus on extracting relevant features from the analyzed blood vessel patterns. Features such as the branching patterns, density, and curvature of blood vessels are identified and quantified for further processing.
Template Generation
Based on the extracted features, a digital template is generated to represent the unique characteristics of the individual's retinal blood vessel patterns.
Matching
The captured retinal pattern from the individual's eye is compared against the stored templates in the system's database.
-
Mathematical algorithms measure the similarity between the captured pattern and the stored templates.
-
If the similarity score meets a predefined threshold, the individual's identity is verified, and access is granted.
Database of Retina Templates
The system maintains a secure database containing the stored templates of enrolled users' retinal patterns.
Decision
Based on the outcome of the matching process, a decision is made regarding the user's identity.
-
If the captured retinal pattern matches any of the stored templates within an acceptable margin of error, access is granted.
-
Besides, if no match is found or if the similarity score falls below the predefined threshold, access is denied.
Applications
High-Security Environments
Retina scanning is commonly used in high-security environments such as government facilities, research labs, and financial institutions, where the highest level of authentication is required.
Healthcare
It is also used in healthcare settings for patient identification and access control to sensitive medical records.
Challenges
User Comfort
Retina scanning requires users to closely align their eyes with the scanning device, which can be perceived as invasive or uncomfortable for some individuals.
Cost and Complexity
The equipment needed for retina scanning tends to be bulky and expensive, limiting its widespread adoption in consumer-facing applications.
Technical Limitations
Certain eye conditions or abnormalities, such as retinal diseases or ocular trauma, may affect the quality and reliability of retina scans.
Fingers: The Time-Tested Biometric Identifier
A. Fingerprint recognition technology
1. Principles of fingerprint recognition
Every fingertip contains a unique pattern of ridges and valleys, known as minutiae. These features don’t change over time, making them ideal for long-term identity verification. Fingerprint systems don’t store actual fingerprint images. Instead, they extract specific data points (like ridge endings, bifurcations, and spatial relationships) to form a mathematical template. When you place your finger on a sensor, that data is matched against your saved template.
The matching can be either verification (are you who you claim to be?) or identification (who are you?). In software applications, verification is more common, especially for secure logins. Instead of remembering passwords or tokens, users offer a quick fingerprint scan, something they are, rather than something they know or have.
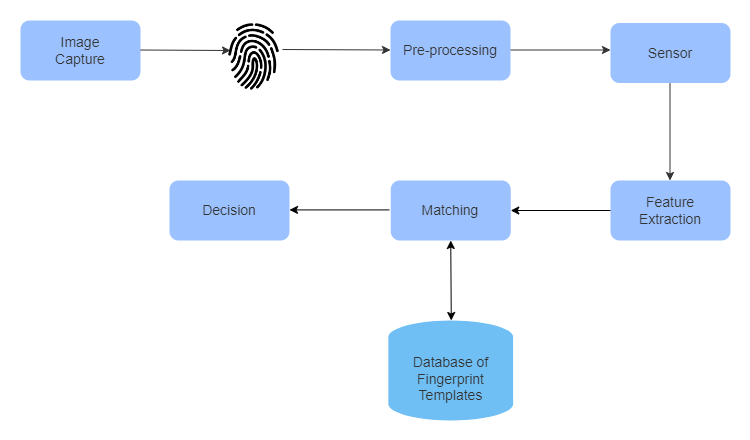
When a user places a finger on a scanner, the system doesn't store the image of the fingerprint. Instead, it extracts measurable characteristics and turns them into a template, a set of mathematical features. The stored template is then used for comparison the next time the user attempts authentication.
2. Evolution and widespread adoption
Fingerprint recognition started gaining digital traction in the early 2000s with government and military projects. But its real momentum began in 2013, when Apple introduced Touch ID on the iPhone 5s. Suddenly, millions of people were unlocking their phones and approving payments with a single tap.
Manufacturers followed suit. Android phones adopted similar features, while laptops like Dell XPS and Lenovo ThinkPads added fingerprint readers to boost security without adding friction. Biometric APIs from Apple (Touch ID) and Google (BiometricPrompt) helped developers bake this feature into their apps.
Today, fingerprint recognition is one of the most common forms of biometric authentication in personal and enterprise devices. Banks started using fingerprints for mobile authentication. Hospitals used them to control access to electronic health records. Governments embedded them in digital ID systems. According to Root Analysis, the fingerprint sensors market size is projected to grow from $6.02 billion in 2024 to $22.1 billion by 2035. Adoption is particularly strong in sectors like cybersecurity, healthcare, and public services, where fast, secure, and passwordless identity verification is a top priority.
B. Advancements in fingerprint recognition
1. Capacitive and optical sensors
Fingerprint recognition has always depended on the hardware behind it. The two dominant types of sensors used today are capacitive and optical, each with different strengths.
Capacitive sensors are now standard in phones and laptops. They use electrical charge differences to detect fingerprint ridges. These sensors are harder to fool because they require actual skin contact, making them resistant to spoofing attempts like silicone molds or photos.
Optical sensors use light to scan and create a digital image of the fingerprint. They're common in entry-level devices and physical access systems. While they are less secure, they’re cheaper to produce and simpler to maintain. Optical sensors are still widely used in places like biometric attendance systems or low-cost tablets.
Ultrasonic sensors use sound waves to capture highly detailed 3D maps of the fingerprint. These can even scan through dirt, sweat, and moisture, making them more practical for field workers or healthcare settings.
Here’s a visual to clarify the differences:
Sensor Type
|
Security Level
|
Cost
|
Common Usage
|
|
Capacitive
|
High
|
Moderate
|
Smartphones, Laptops, POS Devices
|
|
Optical
|
Medium
|
Low
|
Access Control, Kiosks, Entry Systems
|
|
Ultrasonic
|
Very High
|
High
|
Premium Smartphones (e.g., Samsung)
|
2. Integration in smartphones and other devices
Once sensors became smaller and cheaper, manufacturers began embedding fingerprint readers into nearly every class of consumer device. Smartphones were first, followed by tablets, smartwatches, USB drives, and smart locks. But what pushed fingerprint biometrics into relevance was how they started working with software and the cloud.
In a typical cloud-integrated setup, the fingerprint never leaves the device. Instead of sending raw fingerprint data over the internet, the system uses on-device authentication. The fingerprint unlocks a cryptographic key, which then proves the user’s identity to cloud platforms like Microsoft Azure, AWS, or Google Workspace. This architecture is based on FIDO2 and WebAuthn standards.
This approach dramatically lowers the risk of data breaches. Fingerprint authentication is now a common login method for cloud software platforms, including:
Microsoft Azure AD: Used with Windows Hello and biometric-compatible enterprise logins.
Google Workspace: Supports passwordless login using biometric-enabled security keys.
Salesforce, Zoom, Slack, Trello: Integrated with third-party biometric login platforms.
Faces: The Rise of Facial Recognition
A. Facial recognition technology
1. How facial recognition works
Facial recognition systems map and compare key features of the human face. These features include the distance between the eyes, the width of the nose, the shape of the cheekbones, and the contour of the jawline. These landmarks, when captured through a camera, are translated into a unique facial template, often a mathematical vector or matrix, that’s stored and used for future comparison.
According to Allied Market Research, the Global Face Recognition Device Market is projected to reach $16.5 billion by 2032.
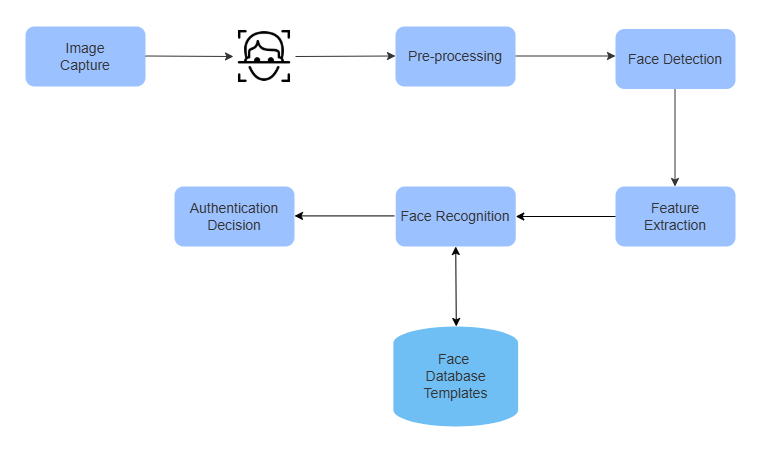
The process begins with face detection, where the system identifies a human face in an image or video frame. Once detected, the system aligns the face, adjusts for lighting or orientation, and extracts specific features using algorithms, deep learning models trained on massive datasets. The extracted template is then compared against a database to verify identity (1:1) or search for a match (1:N).
Unlike passwords or fingerprints, facial recognition can work passively, users don’t need to touch a sensor or input a code. This makes it especially attractive for contactless authentication in public or high-throughput environments. This cycle happens in milliseconds and can support thousands of comparisons per second in cloud-enabled systems.
2. Applications in security and beyond
Facial recognition has become a key part of both consumer tech and enterprise-grade software platforms. At the most basic level, people use it to unlock smartphones, authorize mobile payments, or log into apps like banking platforms, email, or ride-sharing services. But its applications now stretch far wider.
Airports are integrating facial recognition into check-in, immigration, and boarding processes. For example, Delta Air Lines uses facial recognition in Atlanta and Detroit for international flights, shaving several minutes off per passenger interaction.
Retailers have tested facial recognition to detect VIP customers or banned individuals. Some smart stores use it to tie facial profiles to purchase histories or loyalty programs, though this practice has drawn scrutiny.
Healthcare organizations are testing facial biometrics to verify patients during telemedicine calls and streamline access to medical records.
In the public sector, law enforcement agencies use facial recognition to match CCTV footage against suspect databases. Surveillance applications are growing, with cities across China, the U.S., and the Middle East using live video analysis to detect and identify individuals in real time.
In the cloud, major platforms like Microsoft Azure Cognitive Services, Amazon Rekognition, and Google Cloud Vision API offer facial recognition as a service. These systems allow businesses to embed facial authentication directly into web and mobile apps, with features such as age detection, sentiment analysis, and multi-face tracking, all processed at scale.
B. Ethical considerations and privacy concerns
1. Biases and inaccuracies
Facial recognition doesn’t treat every face the same. Multiple studies have found consistent bias in how accurately these systems perform across different demographics. A well-known report by the National Institute of Standards and Technology (NIST) revealed that some commercial facial recognition systems were 10 to 100 times more likely to misidentify Black and Asian faces compared to white male faces.
This isn’t just a data problem, it’s a development oversight. If training data lacks diversity or the model is skewed toward certain facial features, performance gaps are baked into the system. For software and cloud providers, this is more than a technical flaw, it’s a legal and reputational risk.
Misidentification has serious consequences. In the U.S., multiple wrongful arrests have been linked to facial recognition errors. Retailers and landlords have come under fire for using facial surveillance without consent, especially in underserved communities.
The stakes are high. A mismatch in a phone unlock is annoying. A mismatch in a criminal investigation can be life-altering.
2. Regulation and oversight
As the technology spreads, regulators are catching up. Countries are starting to define how facial recognition can be used, who controls the data, and how consent should be handled.
GDPR in the EU classifies facial data as “biometric data” and restricts its processing without explicit, informed consent. The California Consumer Privacy Act (CCPA) also gives individuals the right to opt out of biometric data collection and request deletion.
Several cities, including San Francisco, Portland (Oregon), and Boston, have banned or restricted the use of facial recognition by public agencies. At the federal level, there are calls in the U.S. Congress for stronger transparency and auditing requirements, especially for law enforcement and commercial use.
Clear regulatory frameworks are still evolving, but the trend is clear: facial recognition without transparency or accountability faces growing pushback.
Implementing Biometric Security in Software and the Cloud
Biometric security has moved beyond novelty and into the core of digital authentication. From unlocking phones to verifying transactions, fingerprints and faces now serve as primary credentials in software systems around the world. As software shifts to cloud-first deployment, biometric authentication is evolving from a device feature to a scalable, service-based model. Businesses are no longer asking if they should use biometrics, they're asking how to build it well.
A. Integration into software applications
1. APIs and SDKs for biometric authentication
Biometric authentication depends on local hardware, fingerprint sensors, cameras, or infrared readers, but the real magic happens in software. This is where APIs and SDKs come in. These toolkits give developers access to biometric functions without building the recognition engine from scratch.
On mobile devices, Android BiometricPrompt and Apple’s LocalAuthentication framework are standard tools. They abstract away the hardware differences between devices and give developers a consistent way to authenticate users via fingerprint or face.
For cross-platform apps, SDKs like FaceTec, BioID, and Veridium offer ready-to-integrate modules for facial recognition, voice, and multimodal biometrics. These SDKs come with anti-spoofing capabilities, liveness detection, and real-time feedback systems that help developers meet compliance standards such as FIDO2, GDPR, and HIPAA.
In some of these models, the user never has to enter a password. Instead, the biometric verification triggers a secure token exchange, which is validated by the app or server.
2. Examples of biometric security in popular software
Biometric authentication is already part of many tools we use every day. Mobile banking apps like HSBC, Wells Fargo, and Chase allow users to log in using fingerprint or face recognition instead of passwords. This reduces login friction and limits phishing risk.
Zoom, Slack, and Dropbox offer biometric login via third-party identity providers that support Face ID or Android biometrics as part of the sign-in process. These providers rely on FIDO2/WebAuthn protocols, which are built for passwordless authentication.
In the healthcare sector, Epic Systems, a top electronic health records platform, integrates biometric login for clinicians using fingerprint sensors built into hospital-issued laptops. This lets providers log in within seconds while maintaining security for patient data.
Even government services are adopting this model. India’s Aadhaar system supports biometric logins for tax filing, ID updates, and benefit claims through fingerprint and iris recognition, powered by a national biometric database and device-level verification.
B. Cloud-based biometric authentication services
1. Advantages of cloud-based solutions
According to Markets And Markets, the global biometric system market size is projected to reach $84.5 billion by 2029. Cloud-based biometrics now represent over 40% of all biometric deployments, driven by the rise of remote work and mobile-first app development.
As businesses move infrastructure to the cloud, they’re looking for ways to scale authentication without managing hardware dependencies or sensitive data directly. Cloud-based biometric services meet this need by providing identity verification as an API.
Platforms like Amazon Rekognition, Microsoft Azure Face API, and Google Cloud Vision offer facial detection, analysis, and verification as on-demand services. These APIs let developers send images or video frames and receive structured biometric data in return.
These platforms work at scale. For example, a retail app can use Azure Face API to verify the identity of thousands of users in parallel, matching faces to profiles in milliseconds. That performance level isn’t possible with only on-device matching.
Cloud-based services also reduce operational overhead. Developers don’t have to manage training datasets, optimize model performance, or handle edge-case spoofing detection. Instead, they rely on the cloud provider’s pre-trained models, which are regularly updated and audited.
2. Security considerations and best practices
Cloud services simplify implementation, but they also raise critical security questions. The most sensitive biometric data, faces, fingerprints, and voiceprints, cannot be treated like standard PII. If leaked or stolen, it can’t be changed.
That’s why most providers now recommend or require on-device biometric matching paired with token-based cloud authentication. In this model, the biometric data stays on the user’s device and never reaches the cloud. Instead, the biometric match unlocks a cryptographic key that signs a token. That token is sent to the server to authenticate the user.
This process supports FIDO2 and WebAuthn standards, which significantly reduce the risk of mass biometric data breaches. Even if an attacker intercepts the request, the private key used to sign the token never leaves the device and cannot be reused.
Other best practices include:
- Encrypting biometric templates using AES-256 encryption at rest and TLS 1.3 in transit.
- Using liveness detection to block spoofing with photos, masks, or video playback.
- Providing users with biometric opt-out and fallback options (such as PIN or email verification).
- Auditing biometric API usage logs to track authentication attempts and anomalies.
Challenges and Future Directions
A. Addressing security vulnerabilities
1. Spoofing and presentation attacks
Biometrics rely on physical traits, fingerprints, faces, and voices. But these aren’t immune to attacks. One major threat is presentation attacks, where attackers attempt to fool a system using fake biometric data.
Examples include printed photos to bypass facial recognition, silicone molds to fake fingerprints, or voice recordings to trick voice authentication systems. A 2023 research study from the European Association for Biometrics showed that 41% of consumer-grade facial recognition systems tested were vulnerable to photo-based spoofing without liveness detection.
Liveness detection is now considered critical. This technique verifies that the biometric input is from a living person. For fingerprints, that might involve detecting electrical conductivity or skin temperature. For facial recognition, systems check for blinking, head movement, or 3D structure using infrared cameras.
Cloud biometric platforms like FaceTec, IDEMIA, and iProov have already embedded liveness detection into their SDKs, helping financial institutions and e-commerce providers block spoofing attempts at the source.
To make matters more serious, deepfakes are emerging as a biometric threat. AI-generated videos and audio can now replicate a person’s appearance or voice with eerie accuracy. As these techniques get better, systems that lack deepfake-resistant safeguards will face growing pressure.
2. Continuous authentication solutions
A single authentication at login isn't always enough. People walk away from devices, share them, or leave sessions open longer than expected. Continuous authentication answers this problem by verifying users throughout their session, not just at the start.
Instead of relying on one-time checks, continuous biometric systems run passive verification in the background. This could include facial recognition via webcam, behavioral biometrics like typing rhythm or mouse movement, or gait recognition from phone sensors.
BehavioSec, a behavioral biometrics company, tracks how users interact with a device and flags deviations from their normal pattern. If someone else starts using the device, the system can trigger a re-authentication or a logout. These tools are gaining traction in sectors like banking, where regulatory requirements are strict.
The challenge here isn’t just tech performance. It’s also about balancing security with privacy and user comfort. People don’t want to feel watched all the time, even if it’s for their own security. The solution lies in transparency, consent-driven design, and using data locally on the device where possible.
|
Biometric Security Threats and Countermeasures
|
|
Threat Type
|
Risk Level
|
Industry Response
|
|
Photo/Video Spoofing
|
High
|
Liveness detection, 3D face models
|
|
Voice Replay Attacks
|
Medium
|
Spectral analysis, real-time interaction prompts
|
|
Fingerprint Mold Replication
|
High
|
Capacitance-based sensors, skin conductivity tests
|
|
Session Hijacking
|
Medium
|
Continuous behavioral biometrics
|
|
Deepfake Identity Spoofing
|
Growing
|
GAN-based spoof detection
|
B. Advancements in biometric technology
1. Multi-modal biometrics
No biometric method is perfect on its own. Fingerprints can be damaged. Faces can change. Voices can be mimicked. Multi-modal biometrics solve this by combining two or more biometric traits into one authentication flow.
This setup improves both accuracy and resilience. If one modality fails or returns a low-confidence score, the system can fall back on another. It also adds another layer of defense against spoofing or sensor failure.
USAA, a financial services provider for military personnel, was one of the early adopters of multi-modal biometrics. Their app supports a combination of face and voice recognition. Samsung Knox offers iris plus fingerprint scanning for enterprise mobile devices. These systems are already showing measurable benefits in fraud reduction and user satisfaction.
In multi-modal systems, decision-making uses score-level fusion. Each biometric input produces a score indicating the likelihood of a match. The system then combines the scores using weights or rules to determine if authentication should proceed.
The key is configurability. Organizations must decide whether all factors are required or just one strong match is enough. This makes multi-modal systems flexible for different risk levels and use cases.
2. Artificial intelligence and machine learning
Biometrics have always involved pattern recognition, but machine learning has transformed what’s possible. Deep learning algorithms now drive feature extraction, template matching, and even spoof detection. These models outperform traditional biometric systems in both speed and accuracy.
AI doesn’t just recognize faces. It can distinguish between twins. It can learn to identify a user’s voice in a noisy environment. It can detect tampered images used in spoofing attacks. It also improves over time as it trains on more data.
For cloud-based services, this matters. A biometric authentication engine built on deep learning can scale across millions of users, adapt to new data, and detect outliers or threats in real time.
|
How Machine Learning Fits Into The Modern Biometric Stack
|
|
Layer
|
Role
|
Example Model Used
|
|
Pre-processing
|
Face alignment, noise reduction
|
CNNs
|
|
Feature extraction
|
Identify unique traits in voice, face, or print
|
ResNet, MobileNet
|
|
Spoof detection
|
Identify photos, masks, or deepfakes
|
GAN classifiers, LSTM
|
|
Behavioral modeling
|
Track user patterns for continuous auth
|
Recurrent Neural Networks
|
|
Decision making
|
Combine multiple scores into access decision
|
Ensemble models
|
AI-driven biometrics are already making an impact in law enforcement, border control, financial services, and mobile app security.
That growth won’t come without new challenges. AI brings potential for bias, especially if training data lacks diversity. Systems trained mostly on certain age groups, ethnicities, or skin tones may produce skewed results. That’s why fairness testing and third-party audits are becoming a standard part of biometric system evaluation.
Conclusion
Biometric authentication has moved from a convenience feature to a key security component in software and cloud systems. Its strength lies in verifying identity based on who someone is, not what they know or carry. That shift matters, especially as digital platforms handle more sensitive tasks, from banking and healthcare to government services and enterprise applications.
Businesses that build secure, user-friendly, and privacy-conscious systems lead this transformation.
Biometrics is not just a feature. They’re shaping how users access software, how trust is built, and how security is enforced in real time. The challenge now is to keep pushing the technology forward without losing sight of the people who use it.
The future of access lies in who we are, not what we remember. The right tools already exist. The next step is to use them responsibly, securely, and at scale.