The year 2020 has been unpredictable and groundbreaking on many fronts. It will not be wrong to say that majority of the events that happened this year were not good. From world economies crashing down to organizations being forced to shut down operations, the year 2020 has been full of challenges. On top of everything, there has been a rise in cybersecurity incidents as well.
Earlier this year, Tesla was informed by an internal employee of an unusual offer. The employee was offered $500,000(1) to install ransomware onto the company’s (Tesla) network. As the employee was alert, he informed the management on time, and the issue was taken care of by the FBI.
This was one of the many cybersecurity cases recorded this year.
Amongst the popular cyber-attacks, ransomware is one of the most dangerous. It is mostly spread through infectious emails or attachments. Once the person clicks on an infected link, the ransomware is installed on his system – blocking his access to all data and files until and unless he pays the ransom to get the decryption key. The year 2020 recorded several other cases of cyber threats and ransomware attacks.
As the threat landscape is continuously evolving, cybersecurity is becoming the top-most concern of the IT managers and Chief Information Security Officers (CISOs) worldwide.
While we cannot guarantee what may happen once the system is hit by ransomware or similar malware, we can give you some cybersecurity tips that you must follow to safeguard your data.
10 personal cybersecurity tips in 2021
The following cybersecurity trends and tips for 2021 encompass some general guidelines that you as an employee or a tech professional can abide by when surfing online or using the internet.
1. Precaution is the key and the very first step
The most basic and obvious tip to protect yourself from cyber-attacks is to take precautions. Even the most complicated ransomware and phishing attacks are sometimes successful because of a petty mistake.
In normal life, do you share your credit card details or personal identification numbers with just anybody?
Your data is equally important. You need to protect it as you would your physical documents or assets. Your date of birth, your government identification number, and most importantly your mobile number can be used as a ransom to extort money.
Hackers can create fake email addresses and websites that look legitimate. They can even take over your social media accounts and drop messages that seem pretty genuine. If you happen to click on any URL they share, you can fall into big trouble.
2. Authenticate, Authenticate, and Authenticate
Authentication should be your top priority if you want to protect your data. Especially, if you are an employee working from home or a CISO looking to protect your company’s data. When it comes to personal data like your bank account details or your private messages and pictures on your social media channels, the authentication process can make your account more secure. Most of the social media channels or cloud storage platforms offer two-factor authentication to their users.

Source: Pexels
It adds another layer of security to your account. Protecting your personal information should never be an afterthought. Attackers can sometimes use you as a bait to reach your company’s confidential data. If you are an employee, you can ask your IT administrator to take you on a VPN (Virtual Private Network) connection. You should ensure that you only connect to safe and private WiFi when working from home. Avoid using free or public WiFi when dealing with confidential information.
3. Avoid pop-ups and emails from suspicious or unknown people
Pop-ups are quite common when surfing the internet. Marketers use pop-ups to promote a particular brand, service, discounts, or offers. Though, as personal computer cybersecurity tip, you must avoid clicking or opening any pop-ups.
By clicking on pop-ups, you can fall prey to phishing attacks. But not all pop-ups are bad. You just need to identify the fake ones. A golden rule to follow would be to avoid pop-ups on unidentified web pages. For example, if you are surfing randomly through sites and a pop-up comes displaying false security warning, you should just close the window. Many users fall into such tricks and end-up revealing their digital identities.
A fake pop-up can contain the following information:
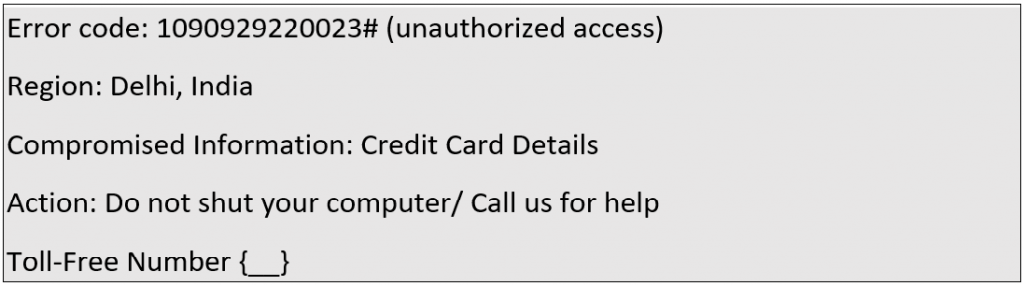
Or,

What you can do to identify fake pop-ups:
- Look for spelling mistakes
- Check the phone number mentioned with that of the security provider. A simple google search would work.
- Try closing your browser. Fake pop-up scams tend to switch your screen to full screen. If the screen is not closing, it is a fake pop-up scam.
- To close such pop-ups, you can open the task manager (CTRL+ALT+DEL), choose the browser in which the pop-up appeared, and then click ‘end task’. Re-open the browser but do not reopen closed tabs.
4. Practise basic password hygiene
We live in a digital age, where we have passwords for everything. From your banking application passwords to your social media accounts passwords, there are plenty of passwords you need to manage daily. Many people have a habit of keeping the same password for all their accounts – after all, it is so easy to remember. If you also do that, it is like an open invitation to be hacked.
Then some people keep easy to guess passwords – like their date-of-births, marriage anniversary, birthdays of closed ones, nicknames, and worst – 123456.
Your passwords are a gateway to your digital identity. If someone manages to breach them, you can land-up in great trouble.
Hackers can get access to your passwords through several types of attacks – brute force attack, credential stuffing, or hash cracking.
But the good news is you can protect your data by following some basic password hygiene:
- Use strong passwords that are a combination of several random letters, symbols, or long paraphrases.
- Change your password at least once every three months.
- Never use the same passwords or reuse an old one. Have a separate password for each service you use.
- Be careful of where you enter your password. Always check the lock sign on the website URL to ensure that the traffic is encrypted.
- You can also enable two-factor authentication. While it is not a tip for having a better password, it can add a new layer of security to your accounts. Even if someone guesses your password, they will be prompted to authenticate the login using an SMS or email sent on your mobile number and email ID.
- Never write down your passwords, especially banking and social media passwords. Use a password manager if you have trouble memorizing them.
5. Always check the URL of the site you are visiting or submitting any information
Whenever you visit a website, you must check the URL in the address bar. Hackers can easily embed malware into sites that look authentic. Even if you are visiting a site you frequently visit, you must check that its URL is correct. You can identify a fake URL by looking for spelling mistakes or HTTP instead of HTTPS. You can also check for the lock sign and security certificate.

Many banking websites advise their customers to type in the net banking URL in the address bar manually instead of just clicking the first link they find in search.
Hackers can take you to a genuine-looking banking site and once you enter your login credentials on that page, your information can be compromised, and you may end up losing your money.
The same rule needs to be followed when opening your social media accounts using a browser. You don’t want someone to get access to your private messages and photos, and later extort money from you using them.
Whenever using net banking, ensure that you use your personal device – preferably a laptop with active anti-virus and anti-malware software running. If you are in doubt, you can use a link verifier to check if the URL you are visiting is blacklisted or not.
6. Keep your software updated
Keeping your operating systems, security software, and other applications updated is integral.
A software update usually involves bug fixes and new security patches.
Whether it’s your smartphone or your work laptop, you must keep them updated.

Source: Pixabay
Anti-virus and anti-malware protection software are frequently updated to respond to emerging cyber threats and new vulnerabilities.
If your company sends out guidelines for security updates, you must install them right away. Do check your privacy settings after every update, as sometimes the new update rolls them back to a prior setting.
7. Be aware of the latest cybersecurity trends and new malware
Viruses and malware are constantly evolving as cybercriminals come up with new ways to attack smartphone and internet users. To ensure that you do not fall prey to one of them, you must keep yourself updated on the latest cybersecurity trends and know what are the top cyber threats?
For example, you might have heard of phishing, but spear phishing is a relatively newer version of the same. While phishing attacks are not targeted, the spear phishing attacks are highly targeted at one organization. The attackers research about the roles of an organization and then can send authentic looking mails to the organization. The aim is to either inject malware into the systems or extort money.
Similarly, there are a lot of new and latest malware that you must be aware of.
You can’t protect yourself completely if you don’t know what the enemy looks like.
Some other malware and viruses include names like Clop Ransomware, fake windows updates, RaaS (Ransomware-as-a-Service), Zeus Gameover, News Malware Attacks, Fleeceware, social engineering, etc.
If you are a Chief Information Security Officer (CISO), you can conduct cybersecurity awareness and training programs in your organization. This will help in keeping the employees updated on what the latest cyber-attack looks like. So, when they come face to face with one, they will be able to take the required action.
8. When it comes to being cyber safe – sharing is not caring
If you want to be cyber safe – remember that in the world of cybersecurity, sharing is not caring.
Never share your passwords and important credentials with anyone, not even the people you trust. They might not misuse it but may accidentally reveal it.
It may sound astonishing, but attackers know a lot about you, your browsing habits, names of your friends and family members, favourite things, habits, and other details that you share on your social media.
So, to be cyber safe, you must share only to your comfort level, nothing beyond it. Why make the job of cybercriminals easier by sharing all your information freely on social media?
Simple details like birthdate or name of the pet can be used to guess your password and further break into your financial data.
Always operate under the premise of – don’t know you, don’t trust you.
Many organizations have stringent IT security policies. Employees are advised not to share passwords in any situation or circumstance.
9. Invest in anti-malware and anti-virus software
Cyberattacks are more complicated than they seem. Sometimes, despite your best efforts, you might come across one. So, to protect your data from being stolen, compromised, deleted, or destroyed, you must invest in a turnkey cybersecurity solution.
The best cybersecurity solution would be the one that promises unified protection – from your endpoints to backup and restoration.
You can turn towards personal cybersecurity services and solutions offered by leading security solution providers like McAfee, Sophos, or Acronis.
For example, Acronis True Image has in-built anti-ransomware defense to protect users against rising cyber threats.
Having an anti-virus and anti-ransomware software installed on your devices can help you safeguard your precious data.
10. Know what to do if you are hacked
We discussed a lot of cybersecurity tips and now let’s talk about the most important thing. What to do if you are hacked?

Source: Pexels
If you think you have accidentally clicked on a suspicious link that may contain malware, you must immediately contact the concerned authority. If it was your work system, you can contact the IT team. If it is your personal system, you can take help from a known security expert. Alternatively, you can take help from your state’s cybersecurity department.
You must also disconnect WiFi, Bluetooth, and storage devices. You don’t want the attack to spread. If you use cloud storage like Dropbox or Google Drive, you can check for versions of your document and files in there.
This article was published on ZNetLive