Summary
It is quite normal practice in manufacturing for certain types of operations to be performed remotely. But past practice has limited this to a highly restricted set of operations and analyses. The COVID-19 pandemic has greatly expanded the need for knowledge workers to be able to perform their work remotely given the current and likely future need for a far more remote workforce.
 This new demand for remote access and remote work is unlikely to disappear anytime soon. So rather than think of additional information infrastructure as a temporary solution addressing the global pandemic, manufacturers need to create new information infrastructure that will enable their knowledge workers to be productive in the future regardless of where they are working.
This new demand for remote access and remote work is unlikely to disappear anytime soon. So rather than think of additional information infrastructure as a temporary solution addressing the global pandemic, manufacturers need to create new information infrastructure that will enable their knowledge workers to be productive in the future regardless of where they are working.
When thinking about secure remote access and remote work for manufacturing, it’s helpful to take a network-centric viewpoint. Manufacturing plants and factories usually have several broad categories of networks and host different applications on each of these. Cybersecurity and standards organizations such as the ISA and the IEC have developed a common and well understood network reference architecture for industrial manufacturing that segments devices and network equipment hierarchically. Based on this segmentation of industrial automation and control systems (IACS), ISA, IEC, and other cybersecurity standards, organizations have identified the levels and logical framework shown in the figure (next page).
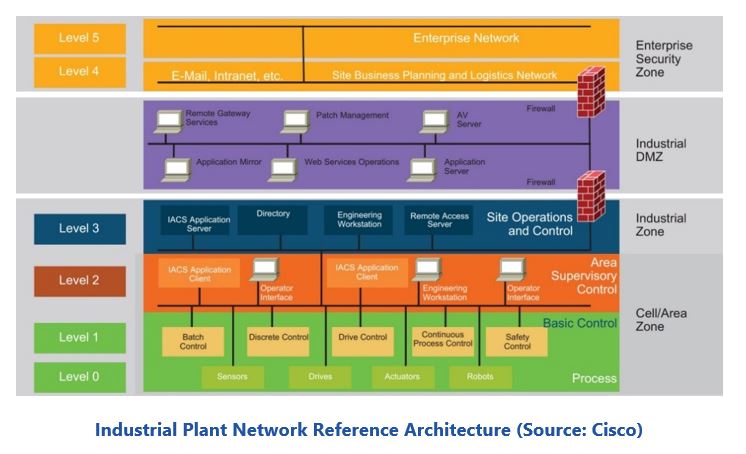
For remote operations and support, the concern is with devices and services at network levels 0 through 3 in the figure. These represent the equipment that performs production, the normal operator and engineering service interfaces, and the information services provided to the enterprise from the plant floor or to sites near the plant floor. Levels 4 and 5 represent IT-administered network functions and business applications. Providing remote access to these services is an enterprise IT concern but not directly related to the plant floor and production. Whereas the services that reside at level 0-3 are much more intimately involved with production operations, quality, etc. These networks host operations that are usually performed by plant or process engineers or by vendors servicing their own equipment.
Cell/Area Zone Operations
These operations and systems are the most critical for production operations and require the most specific training for effective diagnosis and service. Most process plants already have solutions in place to provide remote access to these levels of their production operation for those key individuals responsible for supporting the systems and their strategic vendor partners. In process plants that use DCS for automation there are usually only one or two strategic-level suppliers. These typically provide their own secured remote services and support, which many plants purchase by subscription. In addition, plants deploy other secured remote access solutions to be able to tap into their domain experts’ knowledge without requiring a trip to the site. Discrete manufacturing usually involves a larger set of vendors as well as many more and smaller automation systems. In this case there may be dozens or even hundreds of individuals who need to be granted remote access at certain times. The general practice for these facilities is to implement a secured remote access solution often using a virtual private network (VPN). These types of solutions enable highly granular control of the access rights and privileges of specific end users.
Thus, for their lowest level networks and systems, manufacturers usually have solutions in place for remote access. Since access to these networks and services is necessarily highly restricted, the solutions that are already in place remain serviceable during the period of the pandemic.
Industrial Zone Operations
Operations at level 3 in the network reference model are generally not equipped with remote access. The host computers for these services are located in highly secure physical areas with limited access. During normal operations this restriction is not a problem. But in the time of a pandemic when many more workers are remote, manufacturers would like to provide greater access to these types of information and services, without the restriction of access to a physical network. Generally, these services provide an important window into the real-time operation of the equipment in the plant, whereas higher level services such as analytics, planning, scheduling, and logistics involve longer time horizons and the use of historical rather than real-time plant data.
Pipeline Operations as a Remote Access Model
In the post-COVID-19 era, companies will want to provide more information to more remote workers. The operation of modern oil and gas pipelines provides a useful model for this. In the case of pipelines that may extend 1,000 to 2,000 kilometers, all the workers are essentially “remote” or, at best, can be physically near only a very small fraction of the total operation. They must rely on remote information services to gain a broad view of their operation, which extends over vast distances. The strategy of some of the more recent and successful pipelines has been to replicate remote information services at a central location. This can provide near real-time process information at scale to workers anywhere along the length of the pipeline.
The recently completed 1,850 km TANAP pipeline in Turkey employed this type of strategy to provide information for its central operations from multiple remote locations. TANAP’s strategy was to use OPC extensively and then replicate the OPC services from remote locations to the central control area. This way the pipeline operations could use duplicate OPC client applications in both the remote locations and the central control area.
The TANAP pipeline used Skkynet’s Cogent Datahub product to replicate OPC servers located throughout the pipeline. These installations included application monitoring and could be deployed without modifying the industrial firewalls and security policies in place.

What about the case of a centralized industrial site with many newly remote workers? A similar strategy could be used. OPC services from the Industrial Zone (level 3) could be replicated at level 5, where workers access them using the existing IT infrastructure. Skkynet also provides a cloud-based replication service (see figure). Neither solution requires firewall modification, but the cloud service does not require the capital investment and management in new servers, which is a speed-of-deployment benefit and a potential cost advantage, depending upon the usage patterns.
Conclusion
Regardless of whether they choose cloud-based or hosted applications, manufacturers need to think about these new information infrastructures as permanent rather than as temporary. Supporting a much larger set of remote knowledge workers will be critical for success in the next one to two years and will probably become an expected part of “the new, new normal.
“Reprinted with permission, original blog was posted here”. You may also visit here for more such insights on the digital transformation of industry.
About ARC Advisory Group (www.arcweb.com): Founded in 1986, ARC Advisory Group is a Boston based leading technology research and advisory firm for industry and infrastructure.
For further information or to provide feedback on this article, please contact lkanickaraj@arcweb.com
About the Author:
Harry Forbes
Harry is ARC’s lead analyst for the Distributed Control System (DCS) market. In addition, ARC leverages Harry’s utility expertise in its coverage of Smart Grid, industrial networking, networking and communication standards, and the electric power vertical industry. His research topics include the DCS integration and architecture, Smart Grid, Smart Metering, energy storage, industrial wireless, industrial Ethernet and emerging network technologies.





 This new demand for remote access and remote work is unlikely to disappear anytime soon. So rather than think of additional information infrastructure as a temporary solution addressing the global pandemic, manufacturers need to create new information infrastructure that will enable their knowledge workers to be productive in the future regardless of where they are working.
This new demand for remote access and remote work is unlikely to disappear anytime soon. So rather than think of additional information infrastructure as a temporary solution addressing the global pandemic, manufacturers need to create new information infrastructure that will enable their knowledge workers to be productive in the future regardless of where they are working.