Most of us heard about the dark web via media. People also think that we can buy anything except parents and siblings from the darknet. This document is written to create a kind of awareness about the darknet, what it is, how to get access to it, what it contains, and how it is different from the usual websites which we assess daily. [Read this document only from an academic perspective and I am neither promoting the use of the darknet nor encouraging to use it for unlawful activities.]
What is the Dark web and how it is different from regular websites? The below diagram shows a pictorial representation of the overall internet. What we can access using regular web browsers like Google Chrome, Safari, Internet Explorer, Microsoft Edge is only a small portion of it – say approximately 10% of it. A large majority of the websites are ‘hidden ‘ or ' invisible 'from the regular web search engines and it is called Deep Web.
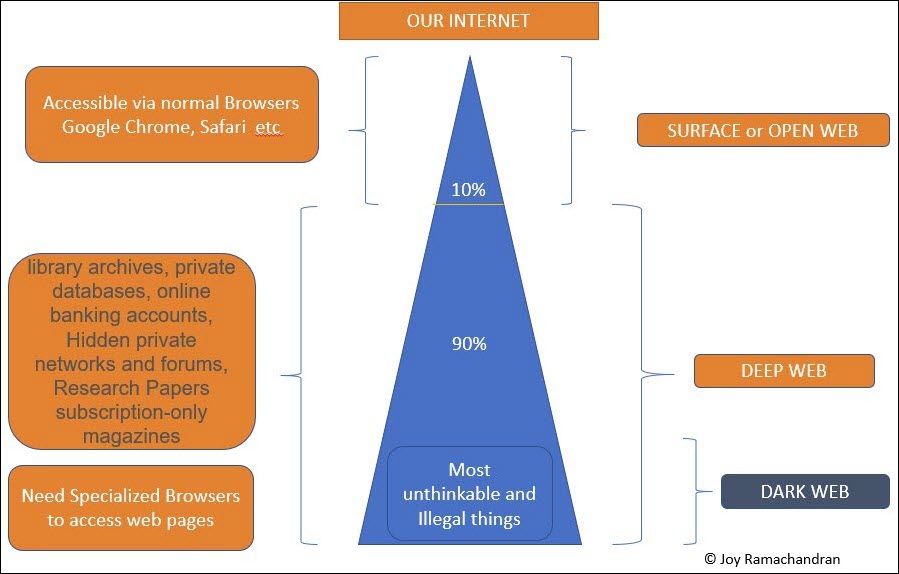
The Dark web is a part of the Deep Web (invisible web ) which has anything which we can think of – unlawful as well as useful. Market places like E-commerce portals sell anything and everything which is beyond your imagination. Some skills and abilities in cyber technology are also needed to do business there, else you land up in trouble by losing money or compromise your computer system to hackers in no time by connecting with the ‘wrong ‘websites. And do not even browse websites for curiosity in the darknet, if you are not sure about the intent of the websites – it can inject malicious payloads into your system and make your systems vulnerable also to harm other networks including your corporate systems. (Note: I use a completely isolated system only for learning and research to access the darknet. An internet service provider can track down and discover the usage of specialized software which you are using to access the darknet. ( yes, there are methods to overcome this also ). Also never try to use your company's digital equipment to connect to these websites )
Deep web access
Deep web content can be accessed with special search engines. A ton of useful articles out there especially for students, researchers, and scientists. The tools which can be used for searching the deep web include google scholar, google news, BizNar, worldwide science. Let’s compare the resulting output of these specialized search engines on the deep web with that of the google.com search engine
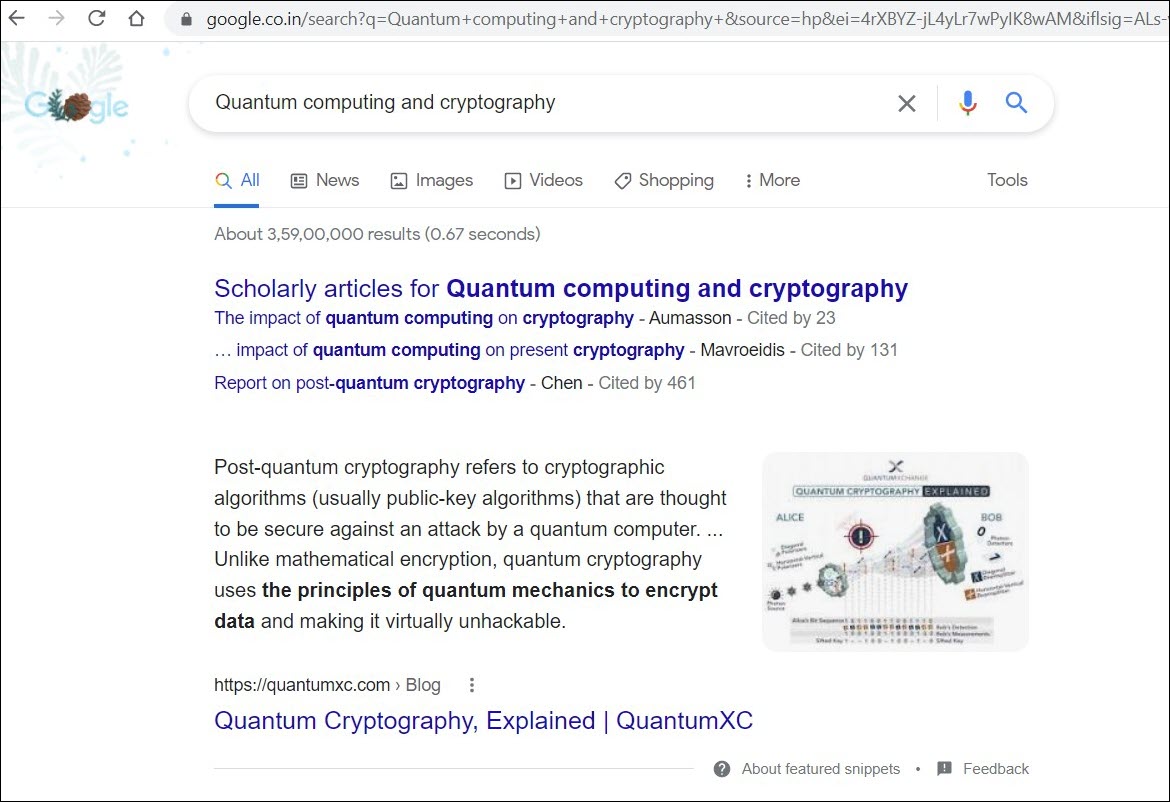
The search string I used is “ quantum computing and cryptography “ in google.com as well as other deep web search engines and look at the outputs given below.
Google.com output
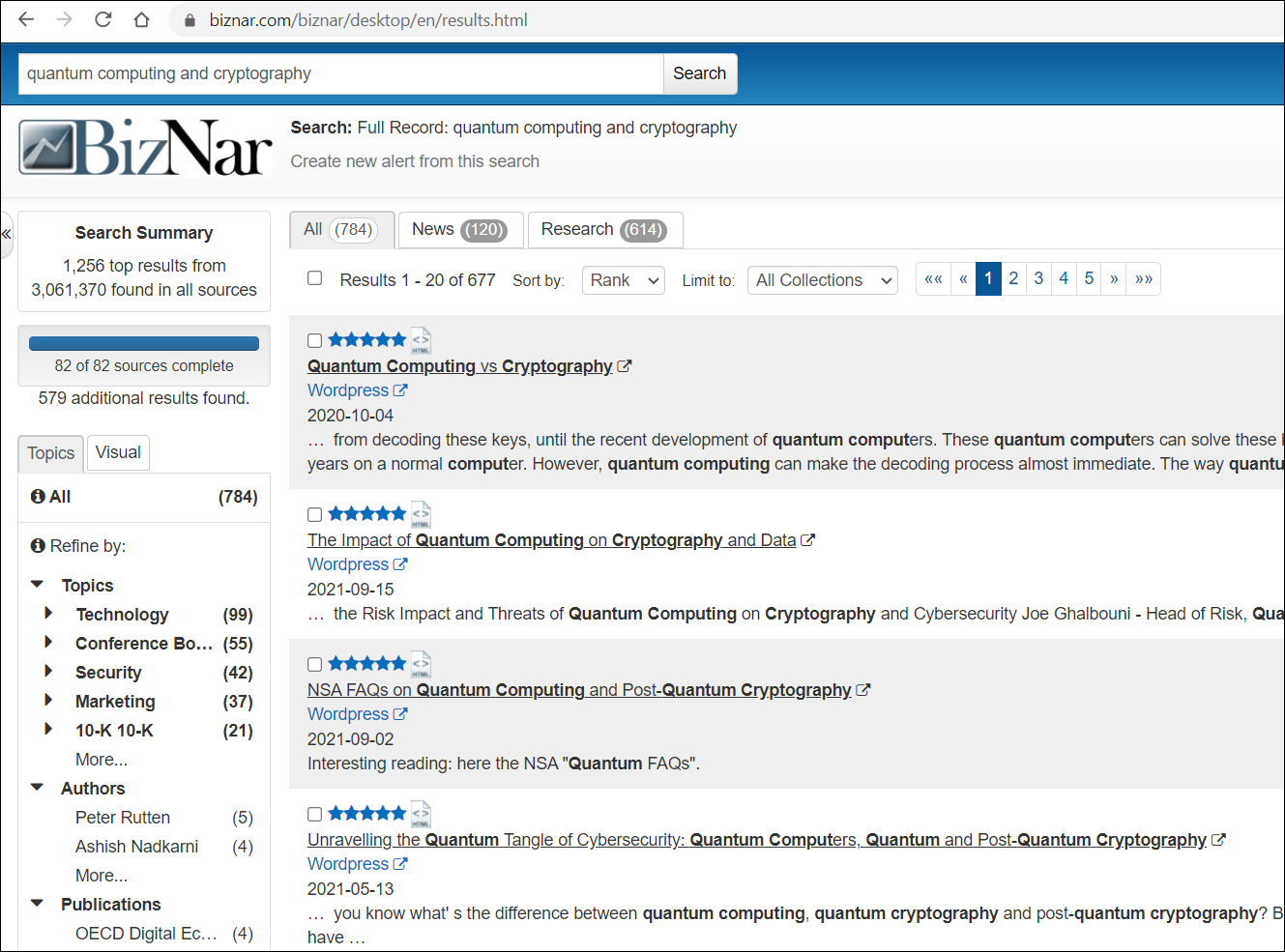
Biznar.com search engine for deep web [Output ]:
Worldwidescience.org search engine for deep web [output]:
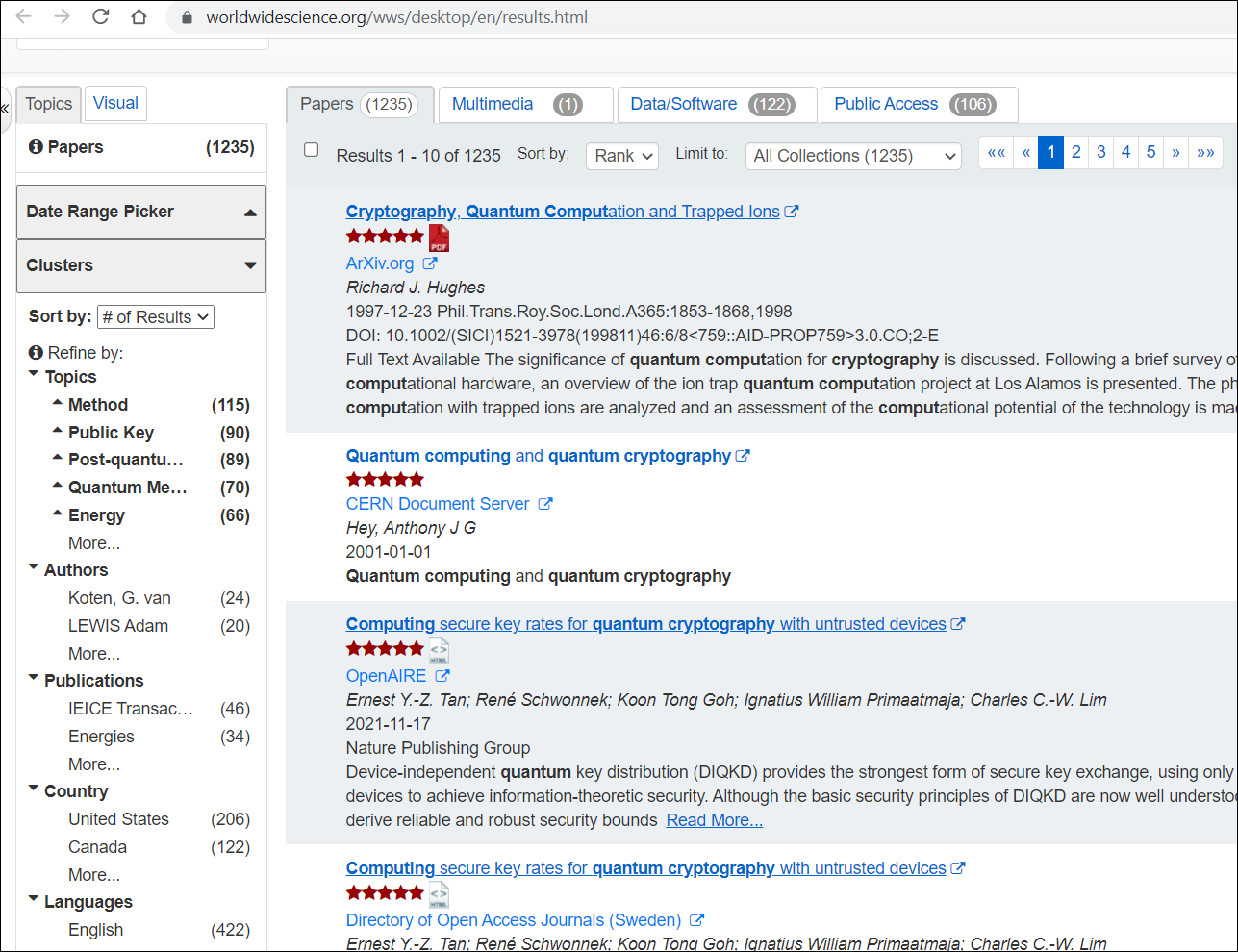
It is very much evident that the search tools used in the deep web give much more details than google.com surface web search engine.
Difference between normal websites and dark websites
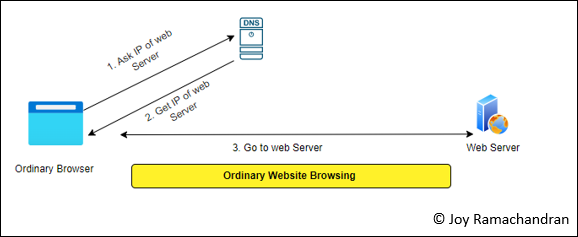
Let us see, how it is different from regular websites which we access using our Google chrome or similar browsers. The below diagram shows the high-level 3 step process which all of us do to access a website from our browsers. If I want to access cnn.com, my browser asks the name server (DNS) the actual address of cnn.com (Public IP of cnn.com). Once the DNS provides it , the browser directly access the web server and contents of cnn.com
But to access websites on the darknet is a complex process as shown in the diagram below. First, we need specialized browsers to access the contents. Second a direct connection from the browser to the website is not possible. The communication is always encrypted, and it is always anonymous. It is complexly private, and the internet service providers cannot easily track what a person is doing over their network.
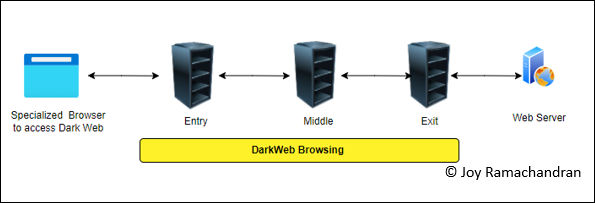
Whenever the user enters a website address in this specialized browser, first the browser contacts an entry server or entry node. The entry server handover the request to a middle node and the middle node to an exit node. The exit node connects with the actual web server and supplies the web content back. The secrecy is kept in such a way that only the entry node knows who is trying to access the webserver. Other servers do not know the user’s IP details. Since the entire request routes through various ‘layers ‘to reach the website, it is called ‘ onion routing ‘ and the browsers are known as ‘onion browsers ‘ and the website address will always end with .onion ( in regular browsers the domains ends with .com, .edu, .org, etc ). The entire communication is encrypted and called tunneled encryption.
How to access the dark web?
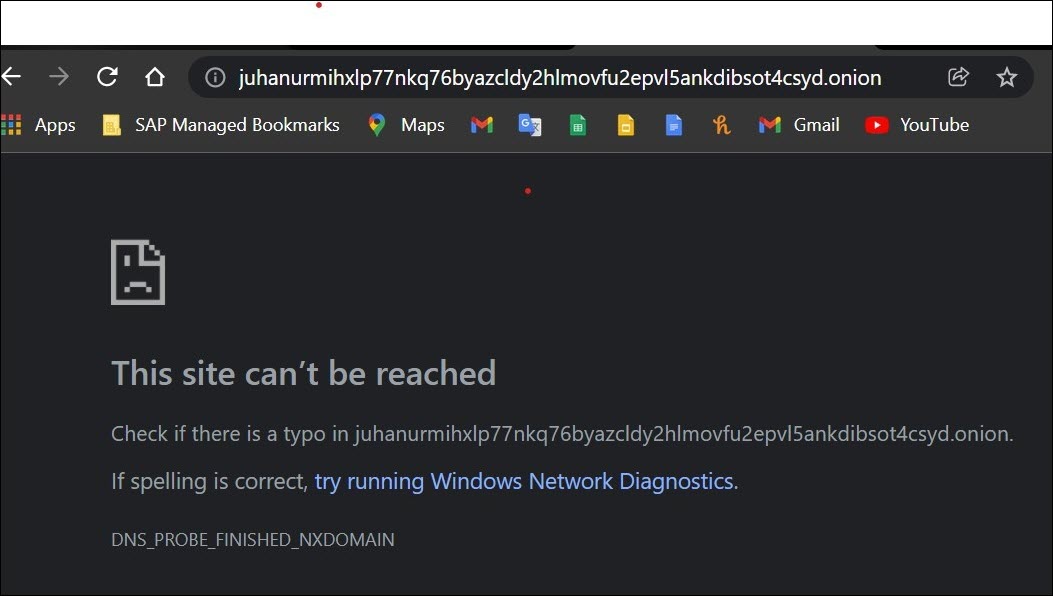
A typical address of a dark web looks like this https://www.sdgdhgfgfsfgdsjhdsds.onion. ( the domain name ends with .onion) . And these addresses will return an error when we use them in ordinary browsers like google chrome (shown below) or internet explorer kind of browsers.
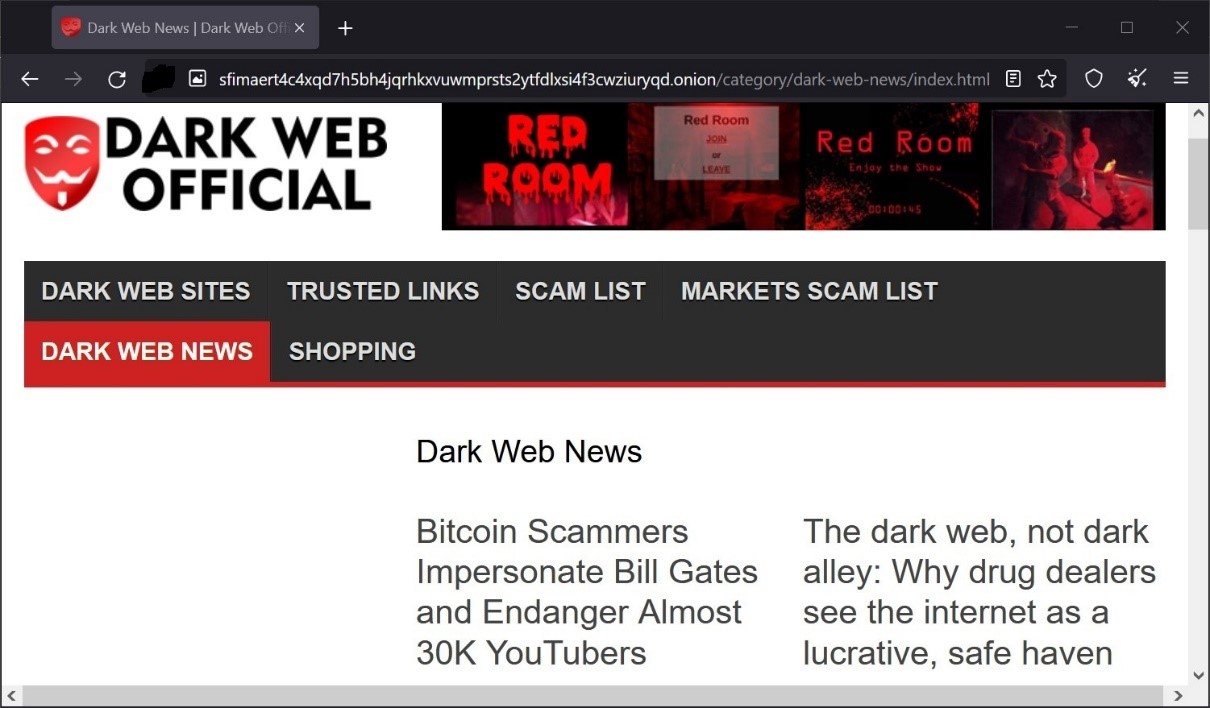
Below is a dark web page accessed using a specialized browser – called an onion browser. For first-time visitors, it looks scary – and it is scary due to the uncommon contents and marketplaces you do not see in usual web browsers like google chrome.
You can notice a few of the sections below. The below web page supplies the names of Trusted websites (vendors and other trustworthy marketplaces on the Dark web) and they also provide a scammers list. But any useful service on the dark web comes with a price tag. Nothing is free here. One should pay using bitcoin or equivalent currency to avail services.
So, if you see something similar like the below – Bitcoin mining as a service or quick download of tools to hack Facebook passwords or a dump of stolen credit card info, do not get excited. The majority are scammers, and you lose your money in no time. There are lots of exciting stuff over there which you never see openly on the surface web – but never throw yourself into the hands of criminals or worst of the worst hackers who kept all kinds of honey pots and wait for the next victim.
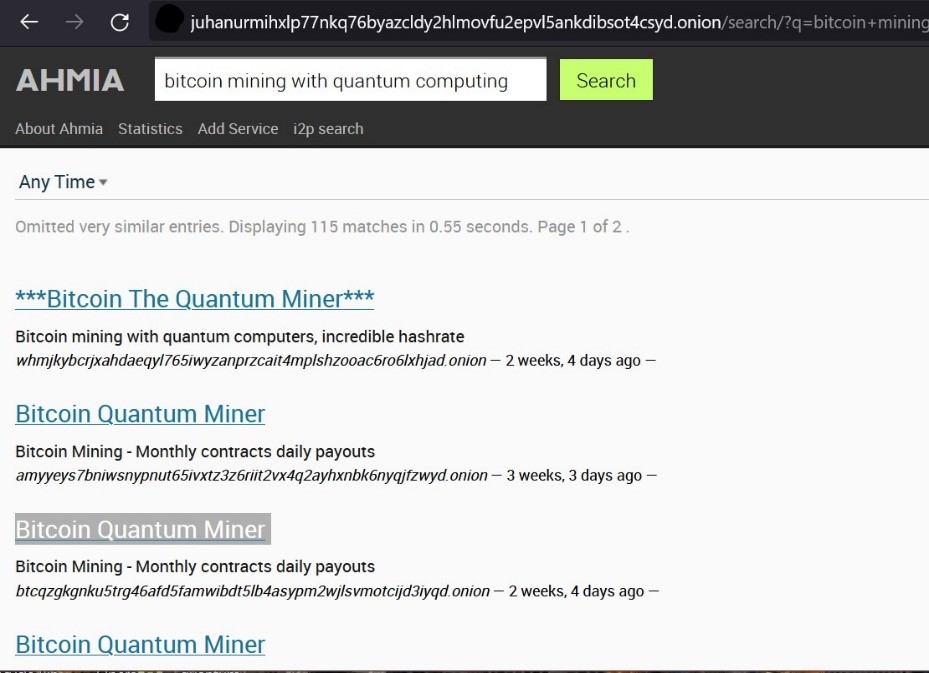
Picture : Bitcoin mining as a service
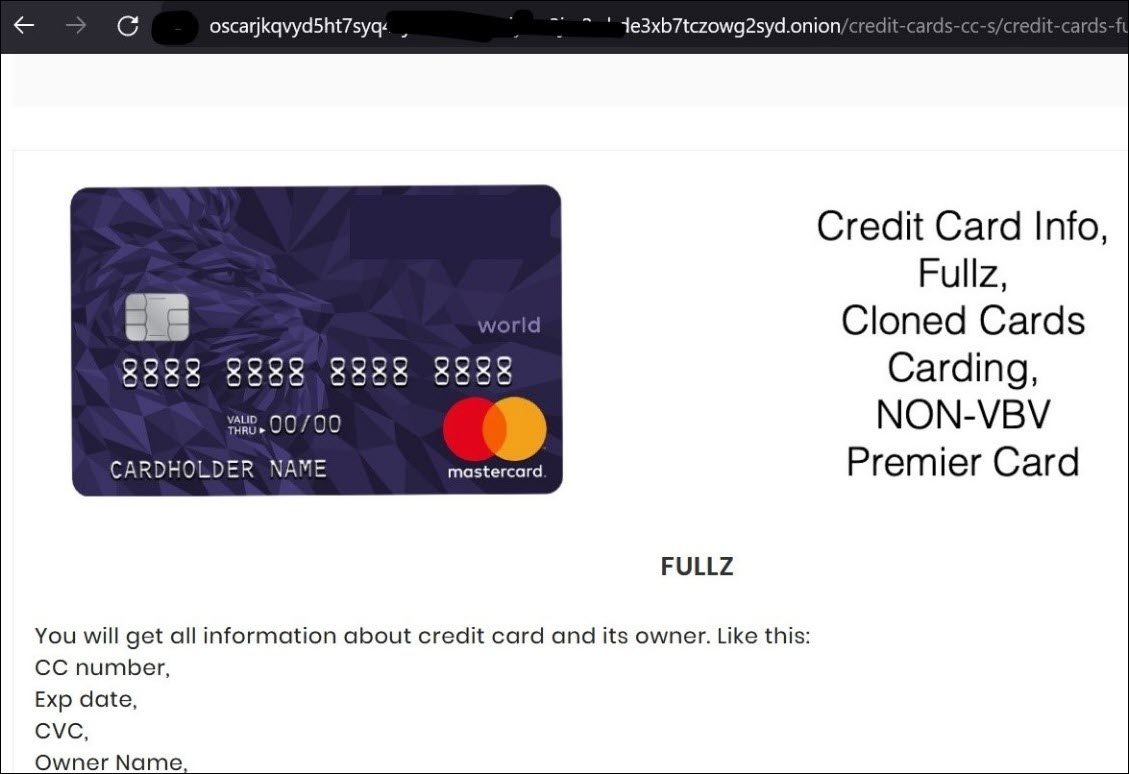
Picture: Stolen credit card data for sale
Who uses the dark web?
Now let me tell you who uses these hidden places on the internet. There is a segment of society who want to keep and share secrets – and also to save their life. There are whistleblowers like Snowdens, oppressed activists, journalists, politicians in countries where there are dictatorships, people who want to hide information for some time from governments also to avoid penalties and imprisonment. Also, there are interested parties who sell and buy explosives, weapons, drugs, counterfeit identity cards, secret records, stolen bank card details – which are prohibited under the law by almost every country in the world. There are IT experts who turned criminals search for malware source codes, social media account hacking or advanced tools to hack into systems and applications, and also terror outfits, gamblers use the darknet for illegal activities.
Other segments that use the dark web and deep web are researchers, penetration testers, academic community – there are a vast number of tools and content available that may not be easily available via normal web browsers. Methods and tools to protect phishing attacks, technical learning, Bitcoin mining using quantum computing power – a few of them I have searched in the dark web, and below are the results. Also, governments and R&D organizations can keep their databases there, which will be concealed from surface web tools.
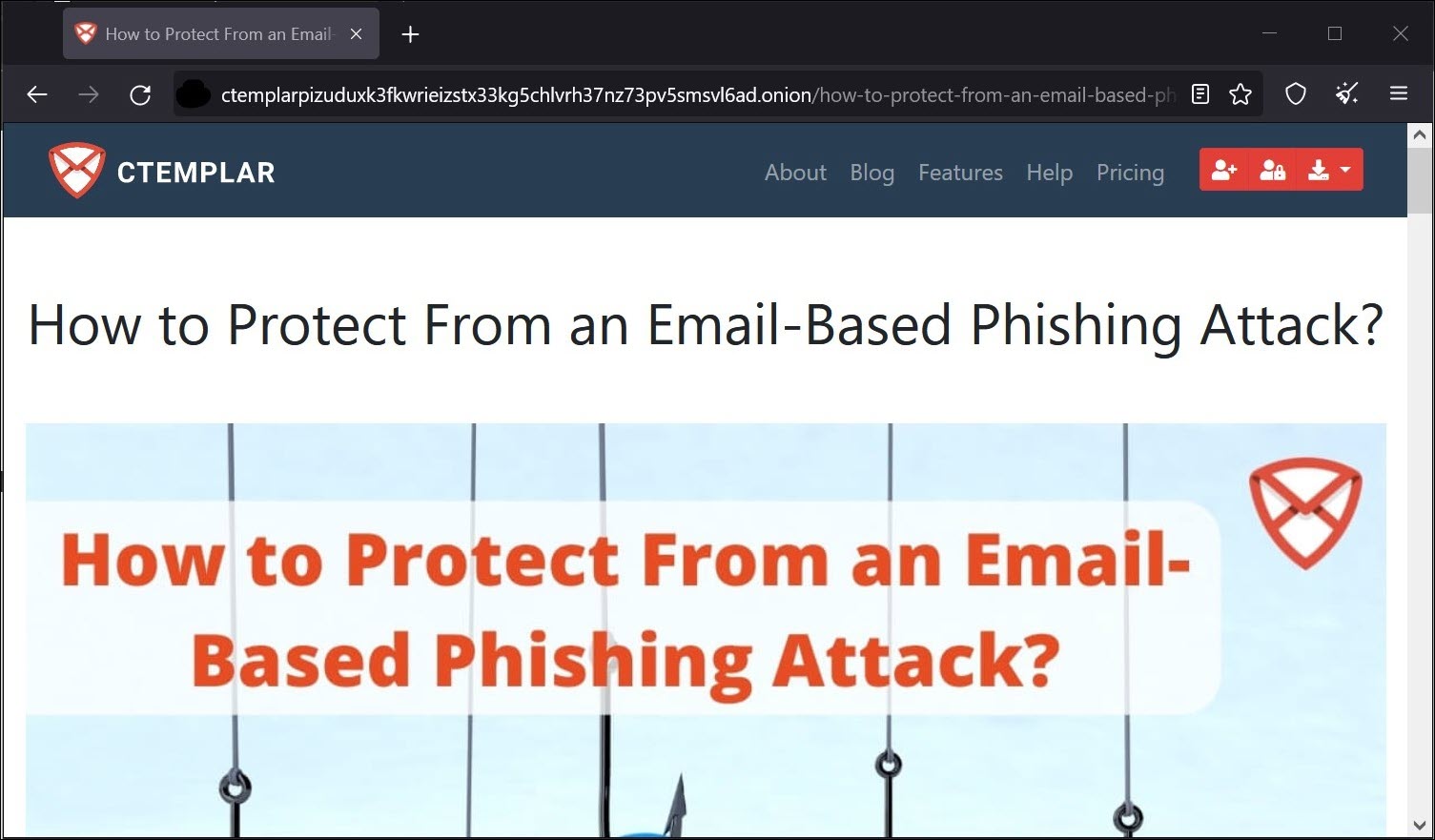
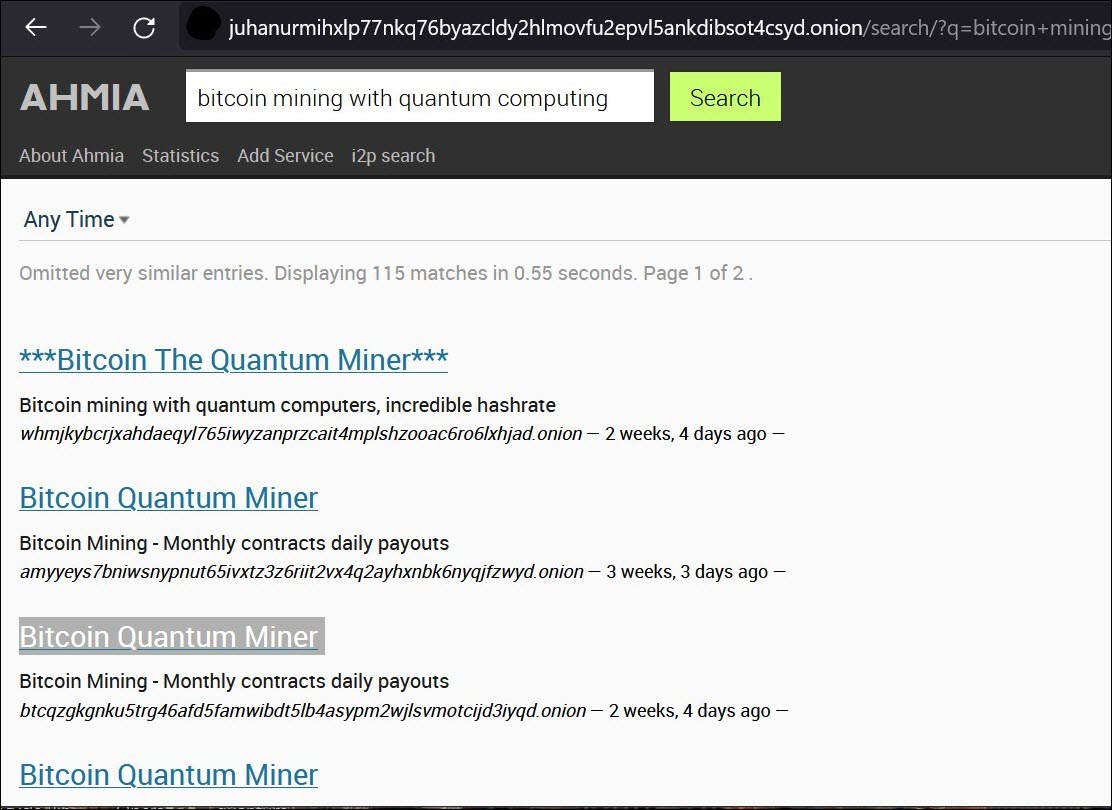
Search Engines used in Dark web.
The search engines used to search contents in Darknet also specialized. Since Google and similar browsers in the surface web will not index the dark web sites, there are specialized dark web search engines available for onion browsers. The one such search engine I have shown below is AHMIA.
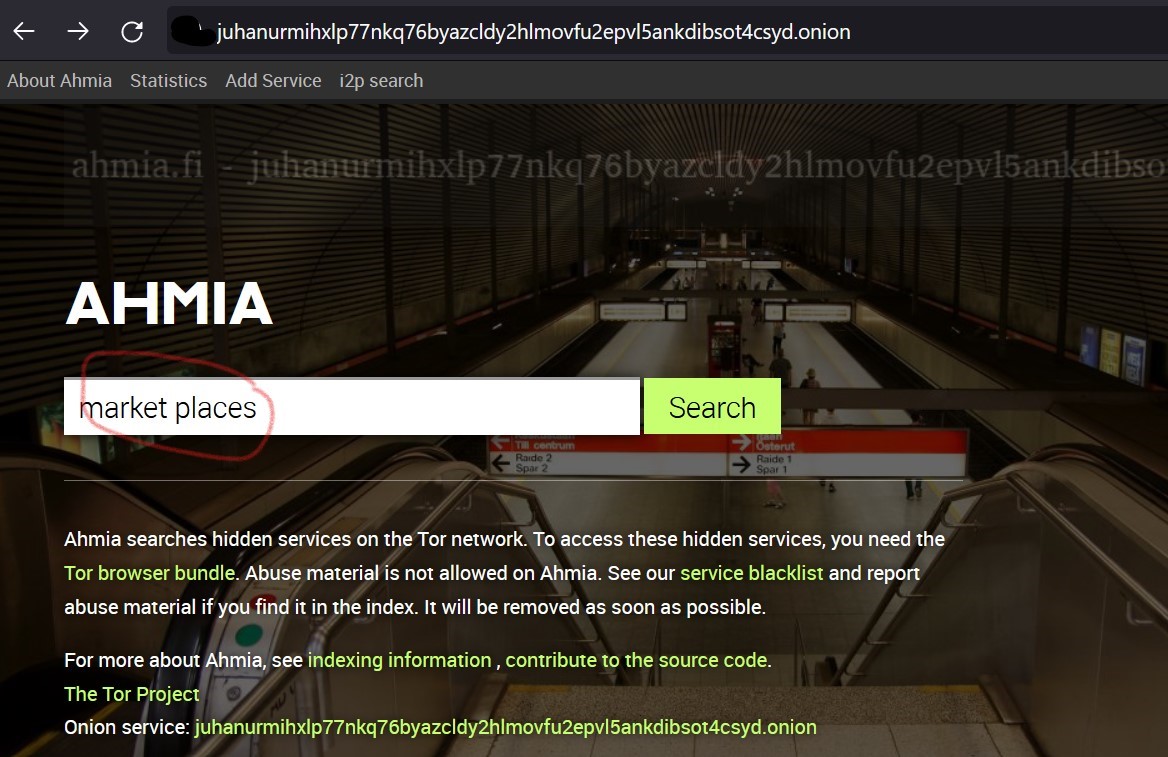
Is accessing the dark web is illegal?
Is browsing the darknet illegal? The answer is Yes and a No. What is the intend – that is the question? If you are a cyber security researcher or student or a forensic investigator and access content that is legal, then fine. If someone uses the contents for illegal or criminal activities which are against law of the land – then one will have to face prosecution. It all depends on what you are doing there. As parents, one should be very clear on what the children are doing with the internet. Many of the parents think and believe that the internet is ONE big source of information. But that is just 10% of your belief. There is a 90% - which is a mysterious underbelly of the internet. The worst of the worst is hidden beneath that surface web. Due to the pandemic, every other student has powerful gadgets, and it is a matter of time for kids to reach the dark web and access those deadly contents. If they do, it is going to be dangerous for them as well as for society. Tools to access these websites are freely available for everyone - that is another threat.
Conclusion
A knife can be used for cutting vegetables and meat to prepare delicious dishes – the same knife can be used for unlawful activities also. The document is written for awareness which many of us do not know – a different world of extreme crime, unlawful and criminal activities and which is growing at an alarming rate. A wrong friend’s or colleagues ‘advice ‘ can put one in jail for the rest of the life – if someone out of curiosity, uses the ‘services ‘ of the vendors out there on the dark web.































Comment
Very useful content to know and create awareness. Thanks Joy.