Anand Patil, Director, Systems Engineering, Cisco India and SAARC
 We are living in strange times. Ever since we started working from home, interactions with humans have been replaced with talking to their rendered images and reconstructed voices. While nothing can replace a three-dimensional meeting, there is no denying that technology has come to our rescue with a viable alternative at a time like this. It has made it possible for me to continue customer interactions with the same regularity as before. Over the last six weeks, I have been able to meet (virtually) with multiple CIOs. Each of these conversations has been incredibly insightful, as they have not only shared their personal experience in dealing with the situation, but also the challenges they faced as an organization, and how they are thinking about the future. While there are some nuances by industry – pharmaceuticals, FSI, ITeS, e-commerce, manufacturing – there are some common themes that have emerged.
We are living in strange times. Ever since we started working from home, interactions with humans have been replaced with talking to their rendered images and reconstructed voices. While nothing can replace a three-dimensional meeting, there is no denying that technology has come to our rescue with a viable alternative at a time like this. It has made it possible for me to continue customer interactions with the same regularity as before. Over the last six weeks, I have been able to meet (virtually) with multiple CIOs. Each of these conversations has been incredibly insightful, as they have not only shared their personal experience in dealing with the situation, but also the challenges they faced as an organization, and how they are thinking about the future. While there are some nuances by industry – pharmaceuticals, FSI, ITeS, e-commerce, manufacturing – there are some common themes that have emerged.
For instance, the magnitude of this crisis has prompted businesses to make reactive decisions, due to which they are reviewing and re-writing their BCPs in the context of the pandemic. Conserving cash has become a priority for most organizations to tide over these times of lean business. IT projects are being closely scrutinized or re-prioritized, and those without a tangible ROI in the medium-term are either being deferred or canceled. At the same time, there is a sharper focus on cloud, automation, AI/ML, robotics, IoT, and above all, cybersecurity. As a result, digitization efforts will gain momentum, especially in processes like packaging, logistics, manufacturing, etc. We will also see a higher percentage of the workforce transitioning to “Working from Anywhere” permanently. The road to full recovery could be a long one, and therefore, we will have to pivot existing plans to operate in the new normal post COVID-19.
Overall, there is a realization that technology can be leveraged to ensure business continuity, even in extreme circumstances. Therefore, enterprise IT architectures will now have to be re-imagined, considering the new future of work, which is where the concept of the “Resilient, Distributed Enterprise” becomes critical.
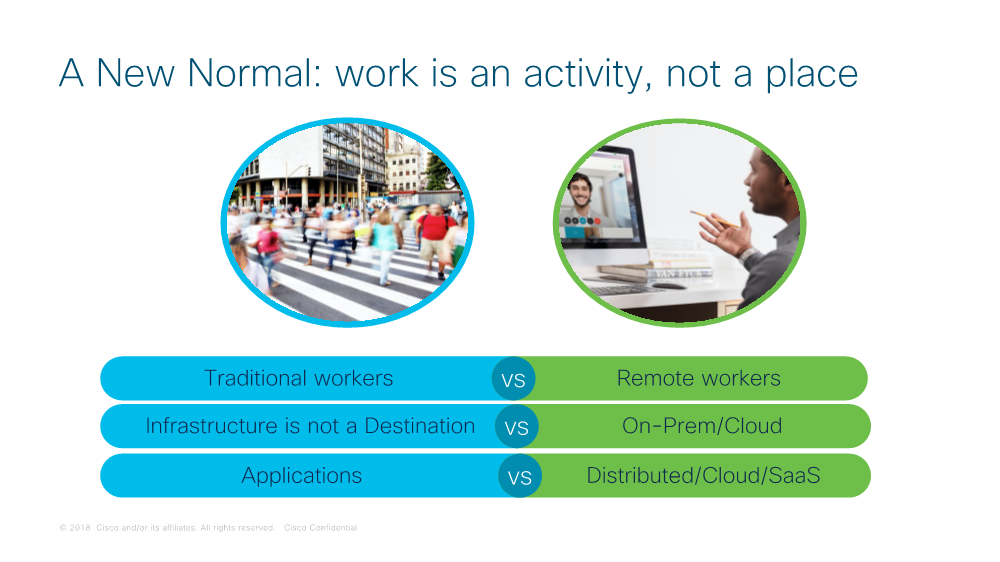
Imagine a scenario where you are the CIO of an enterprise where the users – both internal and external – are distributed over offices, temporary workplaces, and remote locations like homes and coffee shops. They access corporate applications on any device and through any network – public or private. The applications themselves are distributed across on-prem data centers (owned/co-lo) and the public cloud (IaaS/PaaS/SaaS). In this “borderless” environment, how do you ensure consistency of experience, compliance, and security? That’s where the “Resilient, Distributed Enterprise” comes in.
In such an enterprise, the “app” is the business. So, the traditional building blocks of IT infrastructure, such as user access, connectivity, perimeter security, and application hosting, are irrelevant. It helps to start thinking about these IT “capabilities” instead, that can be supported regardless of location, device, and hosting platform.
User Management
In a borderless enterprise, user identity becomes the core element that determines everything else in the process. Most companies today have a centralized identity repository, which can be federated with various service providers as needed. Organizations must leverage this repository for implementing role-based policy authorization (e.g., access to HR vs. finance apps) at multiple levels of access (CFO vs. financial analyst). Combined with Single Sign-On (SSO), which allows employees to use a set of login credentials to access multiple applications, this will make for seamless user experience for application access.
Device Management
The second critical piece in this chain is the device itself, which is of three types: company-owned, company-managed devices, to which the enterprise has full control and can ensure security and compliance to company requirements, presenting the lowest risk while accessing company assets; user-owned, company-managed devices where the user has to agree to the terms and conditions set down by the enterprise MDM, which exercises a fair degree of control over what is and isn’t allowed on the device itself; and user-owned, user-managed devices, for which the enterprise has the least visibility and control.
In each case, it is critical to check the posture of the device before authorizing access to corporate assets. If minimum requirements are not met, access is denied. This posture-check can be cloud-based, especially for user-owned, user-managed devices.
Also, a tiered access policy can be implemented based on the device. For example, company-owned, company-managed devices can have full access while user-owned, user-managed devices are restricted to basic apps. Another thing to consider is the location of the device – some apps may be accessed from any location, while more critical apps can be “geo-fenced” to office networks or certain geographical areas – for example, infrastructure management tools cannot be accessed from outside the country.
Experience Management
When the “app” is the business, the ability to monitor and manage users’ experience proactively becomes paramount. This can be done through an Application Performance Management platform, which can give end-to-end visibility of the user’s journey while using the app, and also proactively alert when issues occur – either in the app or the infrastructure. This capability needs to work across on-prem data centers and the public cloud while providing visibility and pinpointing anomalies within the application code, network, security, and infrastructure components.
Infrastructure Management
With distributed apps, it is crucial to create a common operating environment to manage all the infrastructure elements – whether private or publicly owned – where the apps reside. The first capability required here is a cloud-agnostic, application-centric management solution that helps securely deploy and manage applications across data center, private and public cloud environments. This should offer a governance-enforcing deployment framework mechanism, cost reporting, and visibility into application performance. The second capability is an infrastructure optimization solution that ensures app performance by automatically scaling up or down resources required for optimal capacity. The third is a visibility platform that provides insights into application dependencies and provides comprehensive telemetry for application segmentation as well as compliance and audit reporting. This visibility platform can also extend itself to the user traffic through RA-VPN.
Robust Collaboration Platforms
With potentially a large portion of the workforce going remote, they must be provided with mechanisms to replace in-person meetings and interactions. This calls for a robust and secure meetings and collaboration platform. Apart from the basic capabilities for instant messaging and conference calls, it should be able to support training programs as well as large-format events. Another useful capability is a secure document-sharing platform, which makes it easier to collaborate on content.
Zero Trust Security
The underpinning of the Resilient Distributed Enterprise is Zero Trust security. Given the open nature of the new architecture, a Zero Trust approach becomes imperative. To simplify the approach, it helps to think about this in the context of the elements of the borderless enterprise.
For users, this includes SSO, Multi-Factor Authentication (MFA), and role-based access control, in addition to DNS-level protection and cloud proxy/firewall for access to cloud apps. For devices, capabilities like endpoint validation, posture checking, Endpoint Detection and Response, anti-malware, and Secure VPN for remote-access are key. And for applications, it includes workload and application protection through group-level and micro-segmentation and implementation of behavioral analytics for anomaly detection.
All these capabilities and solutions need to be platform, cloud, and device-agnostic.
Once this framework is in place, there is enormous potential to implement automation by starting to integrate various systems and tools through APIs. For example, if the app experience for a set of users starts to degrade due to a capacity overrun, the App Performance Management tool can send an alert to the Infra Management tool to scale up resources and resolve the issue automatically. However, implementing automation across the IT infrastructure is a journey, and needs to consider the company’s policies and risk profile. It is good to start small and take one step at a time.
In summary, as we prepare for the new requirements of tomorrow, we must start thinking of our IT infrastructure from the outside-in instead of the traditional way of building apps, data centers, networks, and offices. The concept of a “Resilient, Distributed Enterprise” allows us to envision capabilities that will be required for the future of work – one that encompasses distributed workers, distributed applications and services, served by an underlying, inherently secure infrastructure.




 We are living in strange times. Ever since we started working from home, interactions with humans have been replaced with talking to their rendered images and reconstructed voices. While nothing can replace a three-dimensional meeting, there is no denying that technology has come to our rescue with a viable alternative at a time like this. It has made it possible for me to continue customer interactions with the same regularity as before. Over the last six weeks, I have been able to meet (virtually) with multiple CIOs. Each of these conversations has been incredibly insightful, as they have not only shared their personal experience in dealing with the situation, but also the challenges they faced as an organization, and how they are thinking about the future. While there are some nuances by industry – pharmaceuticals, FSI, ITeS, e-commerce, manufacturing – there are some common themes that have emerged.
We are living in strange times. Ever since we started working from home, interactions with humans have been replaced with talking to their rendered images and reconstructed voices. While nothing can replace a three-dimensional meeting, there is no denying that technology has come to our rescue with a viable alternative at a time like this. It has made it possible for me to continue customer interactions with the same regularity as before. Over the last six weeks, I have been able to meet (virtually) with multiple CIOs. Each of these conversations has been incredibly insightful, as they have not only shared their personal experience in dealing with the situation, but also the challenges they faced as an organization, and how they are thinking about the future. While there are some nuances by industry – pharmaceuticals, FSI, ITeS, e-commerce, manufacturing – there are some common themes that have emerged.



















