Nowadays, all enterprises are digital by default. Digital typically means using new technology, connecting devices, and advanced operating procedures, embracing different work styles, and so on. This brings unmatched opportunities and potential for growth and value creation. However, none of the opportunities can bring rewards without dealing with the associated risks.
According to the World Economic Forum report, cybersecurity breach is one of the five most serious risks that the world is facing today. The cybersecurity threat is increasing drastically with the cost of global cybercrime damages reaching $6 trillion by 2021, as per Cybersecurity Ventures.
To gain cyber resilience and fight cybercrime, organizations continue to spend more on cybersecurity. But, unfortunately, the traditional backup and cybersecurity solutions are no longer enough to deal with today’s threats.
Organizations need modern solutions now to protect their sensitive data, applications, and systems.
Acronis, a leader in cyber security solutions, has devised a new approach to serve the cybersecurity needs of users at every level.
5 Vectors of Modern Cyber Protection
Cyber attackers are intelligent, innovative and increasingly organized. Their methods are advanced, stealthy, and fast. These criminals have benefitted from our freedom within the workplace by identifying vulnerabilities. Thus, IT professionals need to consistently defend against current threats.
Despite the new realities, organizations still rely on legacy IT approaches that are putting them and their business at risk. It is, therefore, crucial that they go for solutions that provide a holistic approach to keep their data, applications, and systems safe.
Acronis’ proven, modern approach strategically addresses the broader spectrum of challenges placed within the acronym SAPAS: Safety, Accessibility, Privacy, Authenticity, Security.
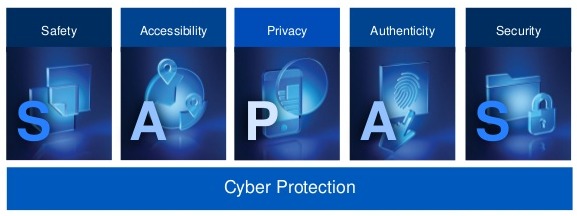
The five problem areas have been transformed and broken down into what Acronis call the Five Vectors of Cyber Protection.
- Safety: Makes sure that a reliable copy of your data is constantly available
- Accessibility: Ensure that your data is readily available from anywhere at any time
- Privacy: Control who has visibility and access to your data
- Authenticity: Have undeniable proof, a copy of your data that is a replica of the original
- Security: Guard your data, applications, and systems against malicious threats
ALSO READ: 3 tips to avoid coronavirus phishing attacks
Balance and Resolve Competing Needs
Admittedly, it is difficult to cover all the five vectors when each of them is often competing with one another. For example, while locking files and folders inside the vault guarantees safety and privacy to the data, it also at the same time makes the data stored inaccessible, and thus, useless from a practical standpoint.
In response, an organization might try deploying various cybersecurity products and services, particularly made to cover each of these vectors. Yet, even if a single point solution might be terrific, using a patchwork approach for protection would create gaps in defenses.
Acronis commits to balance and resolve these competing priorities, which it describes as being #CyberFit.
For an individual, being CyberFit is important and cannot be underestimated. The consequences of data loss can be much more than just an inconvenience. Not only you lose your customers, but also your very existence can be threatened.
Cyber Protection Advice for Organizations
A recent research shows that ransomware attacks against a new organization happens every 11 seconds. However, in spite of the high number of ransomware attacks, 7 out of 10 organizations are not prepared to respond to a cyber-attack.
The impact of lost productivity and unexpected downtime due to cyber-attacks is the reason why C-level executives are being held responsible for their organization’s lost revenues. Infact, many are losing their jobs if security is judged to be lacking.
Industry analysts like IDC recommends Acronis’ cyber protection approach to IT organizations as part of their digital transformation. According to Acronis, you need to:
- Create a cyber protection center that concentrates on data security and availability
- Embrace the right strategy by integrating data protection and disaster recovery (DR)
- Design cyber protection into infrastructure architectures, not as add-ons
- Leverage AI, machine learning and automation to respond better to cyber-attacks
To better understand the benefits, costs and risks associated with Acronis investment, Forrester interviewed the CIO of a high-performance equipment manufacturer who using Acronis’ Cyber Protection solutions for approximately two years for storing and protecting huge volumes of data generated by designing, testing, and deploying its products. He had also been hit by two ransomware attacks and wanted to upgrade the defensive strategy for the future.
The results were compelling and are summarized in the below infographic.
Read the complete report here.