Introduction
Amazon EKS 1.33 is based on Kubernetes 1.33, which was released by the Kubernetes community in April 2025. This version brings numerous enhancements to the Kubernetes platform, and AWS has integrated these improvements while adding AWS-specific features to optimize the experience on their cloud infrastructure.
Key Features and Improvements
1. Enhanced Security Posture
Pod Security Standards Integration
EKS 1.33 deepens integration with Kubernetes Pod Security Standards, making it easier to enforce security policies across namespaces. The enhanced implementation provides more granular controls and improved default configurations aligned with security best practices.
IAM Improvements
Refined IAM Roles for Service Accounts (IRSA) with additional audit capabilities
- Enhanced cross-account access patterns for multi-account architectures
- Improved integration with AWS IAM Identity Center for centralized authentication
Network Policy Enhancements
- Extended Kubernetes Network Policy capabilities with AWS-specific optimizations
- Better integration with AWS VPC CNI for more granular network security controls
- Enhanced visibility into network policy enforcement and violations
2. Operational Excellence
Cluster Lifecycle Management
- Streamlined upgrade paths with reduced downtime during version transitions
- Enhanced node group management with improved scaling algorithms
- More flexible maintenance windows with finer scheduling controls
Observability Improvements
- Native integration with Amazon CloudWatch Container Insights with expanded metrics
- Enhanced logging capabilities with structured logging support
- Improved tracing integration with AWS X-Ray
Resource Optimization
- Advanced bin-packing algorithms for better resource utilization
- Intelligent scaling recommendations based on historical workload patterns
- Cost optimization insights integrated into the EKS console
3. Developer Experience
GitOps Integration
- Native support for GitOps workflows with improved AWS CodeCommit integration
- Enhanced FluxCD and ArgoCD compatibility
- Streamlined CI/CD pipeline integration
Service Mesh Advancements
- Improved AWS App Mesh integration with simplified configuration
- Enhanced traffic management capabilities
- Better observability for service-to-service communication
Developer Tooling
- Enhanced kubectl plugins for EKS-specific operations
- Improved AWS CLI commands for EKS management
- Better IDE integration for local-to-EKS development workflows
4. Scalability Improvements
Cluster Scaling
- Support for larger clusters with up to 1000 nodes (up from 450)
- Improved control plane scaling for high-throughput API operations
- Enhanced etcd performance for large-scale deployments
Workload Scaling
- More responsive Horizontal Pod Autoscaler with predictive scaling capabilities
- Enhanced Vertical Pod Autoscaler with better resource recommendations
- Improved Cluster Autoscaler with faster node provisioning
5. Storage Enhancements
CSI Driver Improvements
- Updated Amazon EBS CSI driver with performance optimizations
- Enhanced Amazon EFS integration for shared storage workloads
- New features for Amazon FSx for Lustre integration for high-performance computing
Volume Management
- Improved snapshot and backup capabilities
- Enhanced volume expansion operations
- Better handling of storage class transitions
6. Networking Advancements
VPC CNI Enhancements
- Higher pod density per node with optimized IP address management
- Reduced latency for pod-to-pod communication
- Better support for custom networking configurations
Load Balancer Integration
- Enhanced AWS Load Balancer Controller with support for additional annotations
- Improved target group management for Network Load Balancers
- Better health check configurations for Application Load Balancers
Service Connectivity
- Enhanced ExternalDNS integration
- Improved service discovery mechanisms
- Better support for hybrid connectivity scenarios
Migration Considerations
Upgrade Planning
Organizations looking to upgrade to EKS 1.33 should consider the following steps:
-
Compatibility Assessment
- Review application compatibility with Kubernetes 1.33
- Test workloads in a non-production environment
- Verify plugin and extension compatibility
-
Resource Planning
- Evaluate control plane capacity requirements
- Review node group configurations
- Assess networking and storage requirements
-
Upgrade Strategy
- Consider blue/green deployment for critical workloads
- Plan for sequential node group upgrades
- Schedule maintenance windows for minimal disruption
Deprecated Features
EKS 1.33 removes support for several deprecated features:
- Legacy API versions that were deprecated in Kubernetes 1.30
- Older container runtime interfaces in favor of containerd
- Certain alpha features that did not graduate to beta
Organizations should review their workloads to ensure they are not dependent on these deprecated features.
Best Practices for EKS 1.33
Security
- Implement Pod Security Standards across all namespaces
- Use IRSA for all service accounts requiring AWS API access
- Implement least-privilege IAM policies
- Enable control plane logging for audit purposes
- Implement network policies for all workloads
Reliability
- Configure multi-AZ node groups for high availability
- Implement proper health checks and readiness probes
- Use managed node groups for simplified lifecycle management
- Configure appropriate resource requests and limits
- Implement proper backup strategies for stateful workloads
Performance
- Optimize instance types based on workload characteristics
- Implement horizontal pod autoscaling for variable workloads
- Use cluster autoscaler for dynamic resource provisioning
- Consider Bottlerocket OS for improved performance and security
- Optimize etcd performance for large clusters
Cost Optimization
- Implement Spot instances for non-critical workloads
- Use Graviton-based instances for better price-performance
- Implement automatic scaling based on demand patterns
- Leverage Savings Plans for predictable workloads
- Use Kubernetes cost allocation tools for visibility
Industry Use Cases
Financial Services
Financial institutions are leveraging EKS 1.33's enhanced security features and scalability improvements to build more resilient and compliant trading platforms, risk management systems, and customer-facing applications.
Healthcare
Healthcare organizations are utilizing EKS 1.33's improved reliability and operational capabilities to deploy patient care systems, medical imaging platforms, and research applications that require high availability and strict data protection.
Retail
Retailers are taking advantage of EKS 1.33's scalability improvements to handle seasonal traffic spikes, implement microservices architectures for e-commerce platforms, and deploy machine learning workloads for personalized shopping experiences.
Manufacturing
Manufacturing companies are using EKS 1.33's edge computing capabilities and improved networking to deploy IoT workloads, predictive maintenance systems, and supply chain optimization applications across distributed environments.
Amazon EKS 1.33 Implementation Guide
Introduction
Amazon Elastic Kubernetes Service (EKS) 1.33 represents the latest managed Kubernetes offering from AWS, providing enhanced security, performance, and operational capabilities. This whitepaper outlines the key features of EKS 1.33 and provides a step-by-step implementation guide for organizations looking to deploy or upgrade to this version.
Key Features of EKS 1.33
- Enhanced Security Posture: Improved security controls, including updated Pod Security Standards and enhanced RBAC capabilities
- Improved Performance: Optimized control plane and data plane operations
- Extended Kubernetes API Support: Support for the latest Kubernetes APIs and features
- Enhanced Observability: Improved logging, monitoring, and tracing capabilities
- Streamlined Cluster Management: Enhanced cluster lifecycle management tools
- Expanded Add-on Support: Additional AWS and partner add-ons for enhanced functionality
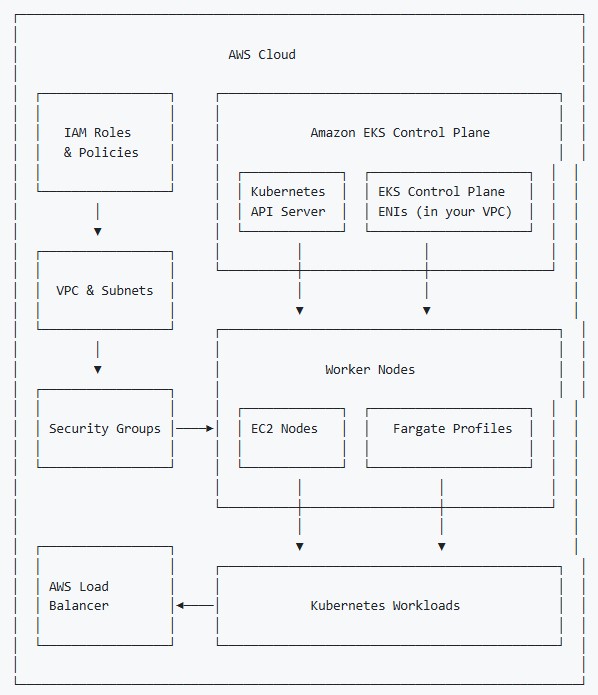
Implementation Steps
1. Prerequisites
Before implementing EKS 1.33, ensure you have the following prerequisites in place:
- AWS CLI installed and configured with appropriate permissions
- kubectl installed (version 1.33 or compatible)
- eksctl installed (latest version)
- AWS IAM permissions to create and manage EKS clusters
- A VPC with at least two public or private subnets in different Availability Zones
# Install or update AWS CLI
curl "https://awscli.amazonaws.com/awscli-exe-linux-x86_64.zip" -o "awscliv2.zip"
unzip awscliv2.zip
sudo ./aws/install
# Install kubectl
curl -LO "https://dl.k8s.io/release/v1.33.0/bin/linux/amd64/kubectl"
chmod +x kubectl
sudo mv kubectl /usr/local/bin/
# Install eksctl
curl --silent --location "https://github.com/weaveworks/eksctl/releases/latest/download/eksctl_$(uname -s)_amd64.tar.gz" | tar xz -C /tmp
sudo mv /tmp/eksctl /usr/local/bin
2. VPC Configuration
Create a VPC with the necessary subnets, route tables, and security groups:
# Create VPC using CloudFormation template
aws cloudformation create-stack \
--stack-name eks-vpc \
--template-url https://s3.amazonaws.com/amazon-eks/cloudformation/2020-10-29/amazon-eks-vpc-private-subnets.yaml
3. Create EKS Cluster
Create an EKS 1.33 cluster using eksctl:
# Create cluster configuration file
cat > eks-cluster.yaml << EOF
apiVersion: eksctl.io/v1alpha5
kind: ClusterConfig
metadata:
name: eks-1-33-cluster
region: us-east-1
version: "1.33"
vpc:
id: vpc-xxxxxxxxxxxxxxxxx # Replace with your VPC ID
subnets:
private:
us-east-1a:
id: subnet-xxxxxxxxxxxxxxxxx # Replace with your subnet ID
us-east-1b:
id: subnet-xxxxxxxxxxxxxxxxx # Replace with your subnet ID
managedNodeGroups:
- name: managed-ng
instanceType: m5.large
desiredCapacity: 2
minSize: 2
maxSize: 4
privateNetworking: true
iam:
withAddonPolicies:
imageBuilder: true
autoScaler: true
albIngress: true
cloudWatch: true
ebs: true
EOF
# Create the cluster
eksctl create cluster -f eks-cluster.yaml
4. Configure kubectl
Configure kubectl to communicate with your new EKS cluster:
aws eks update-kubeconfig --name eks-1-33-cluster --region us-east-1
5. Install Essential Add-ons
Install essential EKS add-ons:
# Install AWS VPC CNI
eksctl create addon --name vpc-cni --cluster eks-1-33-cluster --version latest
# Install CoreDNS
eksctl create addon --name coredns --cluster eks-1-33-cluster --version latest
# Install kube-proxy
eksctl create addon --name kube-proxy --cluster eks-1-33-cluster --version latest
# Install AWS Load Balancer Controller
eksctl create iamserviceaccount \
--cluster=eks-1-33-cluster \
--namespace=kube-system \
--name=aws-load-balancer-controller \
--attach-policy-arn=arn:aws:iam::123456789012:policy/AWSLoadBalancerControllerIAMPolicy \
--approve
helm repo add eks https://aws.github.io/eks-charts
helm repo update
helm install aws-load-balancer-controller eks/aws-load-balancer-controller \
-n kube-system \
--set clusterName=eks-1-33-cluster \
--set serviceAccount.create=false \
--set serviceAccount.name=aws-load-balancer-controller
6. Configure Cluster Autoscaler
Deploy and configure the Kubernetes Cluster Autoscaler:
# Create IAM policy for Cluster Autoscaler
cat > cluster-autoscaler-policy.json << EOF
{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"autoscaling:DescribeAutoScalingGroups",
"autoscaling:DescribeAutoScalingInstances",
"autoscaling:DescribeLaunchConfigurations",
"autoscaling:DescribeTags",
"autoscaling:SetDesiredCapacity",
"autoscaling:TerminateInstanceInAutoScalingGroup",
"ec2:DescribeLaunchTemplateVersions"
],
"Resource": "*",
"Effect": "Allow"
}
]
}
EOF
aws iam create-policy \
--policy-name AmazonEKSClusterAutoscalerPolicy \
--policy-document file://cluster-autoscaler-policy.json
# Create service account for Cluster Autoscaler
eksctl create iamserviceaccount \
--cluster=eks-1-33-cluster \
--namespace=kube-system \
--name=cluster-autoscaler \
--attach-policy-arn=arn:aws:iam::123456789012:policy/AmazonEKSClusterAutoscalerPolicy \
--override-existing-serviceaccounts \
--approve
# Deploy Cluster Autoscaler
kubectl apply -f https://raw.githubusercontent.com/kubernetes/autoscaler/master/cluster-autoscaler/cloudprovider/aws/examples/cluster-autoscaler-autodiscover.yaml
# Patch the deployment to add cluster name
kubectl -n kube-system patch deployment cluster-autoscaler --patch \
'{"spec":{"template":{"spec":{"containers":[{"name":"cluster-autoscaler","command":["./cluster-autoscaler","--v=4","--stderrthreshold=info","--cloud-provider=aws","--skip-nodes-with-local-storage=false","--expander=least-waste","--node-group-auto-discovery=asg:tag=k8s.io/cluster-autoscaler/enabled,k8s.io/cluster-autoscaler/eks-1-33-cluster","--balance-similar-node-groups","--skip-nodes-with-system-pods=false"]}]}}}}'
# Add Cluster Autoscaler annotation
kubectl -n kube-system annotate deployment.apps/cluster-autoscaler cluster-autoscaler.kubernetes.io/safe-to-evict="false"
7. Configure Monitoring and Logging
Set up monitoring and logging for your EKS cluster:
# Install CloudWatch Container Insights
ClusterName=eks-1-33-cluster
RegionName=us-east-1
FluentBitHttpPort='2020'
FluentBitReadFromHead='Off'
[[ ${FluentBitReadFromHead} = 'On' ]] && FluentBitReadFromTail='Off'|| FluentBitReadFromTail='On'
[[ -z ${FluentBitHttpPort} ]] && FluentBitHttpServer='Off' || FluentBitHttpServer='On'
curl https://raw.githubusercontent.com/aws-samples/amazon-cloudwatch-container-insights/latest/k8s-deployment-manifest-templates/deployment-mode/daemonset/container-insights-monitoring/quickstart/cwagent-fluent-bit-quickstart.yaml | sed 's/{{cluster_name}}/'${ClusterName}'/;s/{{region_name}}/'${RegionName}'/;s/{{http_server_toggle}}/"'${FluentBitHttpServer}'"/;s/{{http_server_port}}/"'${FluentBitHttpPort}'"/;s/{{read_from_head}}/"'${FluentBitReadFromHead}'"/;s/{{read_from_tail}}/"'${FluentBitReadFromTail}'"/' | kubectl apply -f -
# Install Prometheus and Grafana using Helm
kubectl create namespace monitoring
helm repo add prometheus-community https://prometheus-community.github.io/helm-charts
helm repo update
helm install prometheus prometheus-community/kube-prometheus-stack \
--namespace monitoring \
--set grafana.enabled=true \
--set prometheus.service.type=LoadBalancer
8. Implement Security Best Practices
Apply security best practices to your EKS cluster:
# Create Pod Security Standards
cat > pod-security-standards.yaml << EOF
apiVersion: kyverno.io/v1
kind: ClusterPolicy
metadata:
name: require-pod-security-standards
spec:
validationFailureAction: enforce
rules:
- name: restrict-host-path
match:
resources:
kinds:
- Pod
validate:
message: "Host path volumes are not allowed"
pattern:
spec:
=(volumes):
- =(hostPath): "null"
EOF
# Install Kyverno policy engine
kubectl create -f https://github.com/kyverno/kyverno/releases/download/v1.10.0/install.yaml
kubectl apply -f pod-security-standards.yaml
# Enable network policies
kubectl apply -f - <
9. Deploy Sample Application
Deploy a sample application to verify your EKS cluster:
# Create a sample deployment
kubectl apply -f - <
10. Verify Deployment
Verify that your EKS cluster and sample application are running correctly:
# Check nodes
kubectl get nodes -o wide
# Check pods
kubectl get pods -A
# Check services
kubectl get services -A
# Get load balancer URL
kubectl get service nginx -o jsonpath='{.status.loadBalancer.ingress[0].hostname}'
Conclusion
Amazon EKS 1.33 represents a significant advancement in managed Kubernetes services, offering enhanced security, improved operational capabilities, and a better developer experience. Organizations looking to adopt or upgrade to EKS 1.33 will benefit from these improvements while leveraging AWS's continued commitment to providing a robust and reliable Kubernetes platform.
By carefully planning migrations, following best practices, and taking advantage of the new features, organizations can maximize the value of their EKS deployments and build more resilient, secure, and scalable applications.
Amazon EKS 1.33 provides a robust, secure, and scalable platform for running containerized applications. By following this implementation guide, you can deploy a production-ready EKS cluster that adheres to AWS best practices for security, reliability, and performance.
References